CVE-2024-36401 Remote Code Execution (RCE) vulnerability in evaluating property name expressions
The GeoServer community has been under considerable strain responding to CVE-2024-36401. This vulnerability stems from GeoTools library CVE-2024-36404.
This vulnerability, in the handling of XPath expressions, affords a “remote code execution” attack that is under active exploit. A remote code execution (RCE) attack allows an attacker to run malicious code on your computer or network.
For more information:
- GeoServer 2.25.2 Release (Jun 18, 2024)
- GeoServer 2.24.4 Release (Jun 18, 2024)
- GeoServer 2.22.6 Release (Mar 17, 2025)
- CVE-2024-36401 (July 1, 2024)
- CISA Warns of Actively Exploited RCE Flaw in GeoServer GeoTools Software (The Hacker News, July 18, 2024)
- GeoServer Vulnerability Targeted by Hackers to Deliver Backdoors and Botnet Malware (The Hacker News, September 6, 2024)
Q: Why have I been directed to this post?
You are responsible for running a GeoServer instance that has not been updated.
-
CVE-2024-36401 provides mitigation instructions which you should perform immediately.
Please stop reading and do this now.
-
Update your instance: Upgrading existing versions (User Guide)
The instructions include notes on upgrading specific versions. Please read carefully to see if any manual changes are required.
Q: Do I have to update or is a patch available?
With such a serious issue several service providers have stepped forward to make fixes available for prior releases.
Full release:
- GeoServer 2.23.6 Release (GeoCat)
Patch provided with CVE-2024-36401 report:
- GeoServer 2.25.1 (GeoSolutions)
- GeoServer 2.24.3 (GeoSolutions)
- GeoServer 2.24.2 (GeoSolutions)
- GeoServer 2.23.2 (GeoSolutions)
- GeoServer 2.22.2 (GeoSolutions)
- GeoServer 2.21.5 (GeoSolutions)
- GeoServer 2.21.4 (GeoSolutions)
- GeoServer 2.20.7 (GeoSolutions)
- GeoServer 2.20.4 (GeoSolutions)
- GeoServer 2.19.2 (GeoSolutions)
- GeoServer 2.18.0 (GeoSolutions)
Free software is a participation sport - to create a patch for a prior release volunteer with community development.
Q: How often should I upgrade GeoServer?
GeoServer operates with a time boxed release cycle, maintaining “stable” and “maintenance” releases, over the course of a year.
-
Upgrade GeoServer twice a year as new stable releases are made.
-
Once the release you are using has entered “maintenance” it is a good idea to upgrade (before the release is no longer supported).
-
GeoServer security policy provides one year of support. You may also contact our service providers for extended support beyond this timeframe.
Q: Notification of security vulnerabilities?
Stay up to date:
-
Please monitor release announcements for the heading “Security Considerations”.
Security Considerations
This release addresses security vulnerabilities and is considered an essential upgrade for production systems.
- CVE-2024-36401 Critical
You can review the release announcement, and in this case with a “Critical” vulnerability decide to update.
-
When everyone has had an opportunity to update the details of the vulnerability are announced.
Security Considerations
This release addresses security vulnerabilities and is considered an essential upgrade for production systems.
- CVE-2024-36401 Remote Code Execution (RCE) vulnerability in evaluating property name expression (Critical)
-
As GeoServer has now adopted use CVEs for publication you may also have success with vulnerability scanning tools.
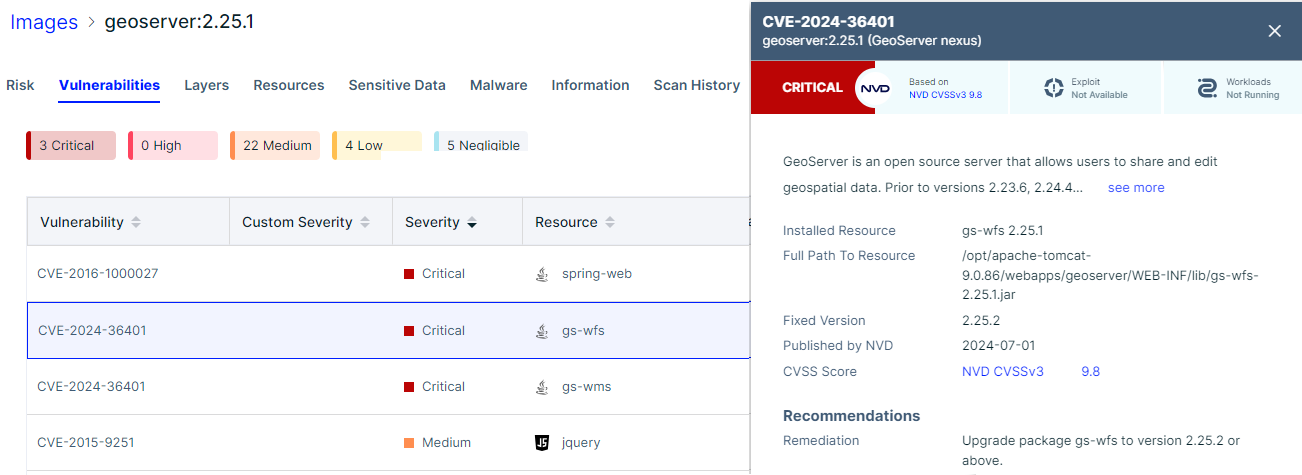
These tools function when the vulnerability is published, and do not provide any advance notice.
Q: Notification of security reports?
As security reports contain sensitive information they are only shared with representatives of the geoserver-security email list.
Participation in geoserver-security, like commit access, is volunteer based and reflects trust.
Please review GeoServer Security Policy if you are in a position to help out.
Behind The Scenes
- GeoServer 3 First public release date
- GeoServer 3 Sprint Update
- GeoServer 2025 Q4 Developer Update
- GeoServer 3 Crowdfunding Goal Surpassed!
- GeoServer 2025 Q2 Developer Update
- GeoServer 3 Crowdfunding – Last Call!
- GeoServer 3 Crowdfunding Campaign Reaches Major Step: 80% Funding Completion
- GeoServer 2025 Roadmap
- GeoServer 2024 Q4 Developer Update
- GeoServer 3 Call for Crowdfunding