June 2025 Vulnerability Disclosures
The GeoServer community has readied the following CVE vulnerabilities for public disclosure.
-
CVE-2025-30220 XML External Entity (XXE) Processing Vulnerability in GeoServer WFS Service (High)
Fixed: GeoServer 2.27.1 | GeoServer 2.26.3 | GeoServer 2.25.7 -
CVE-2025-30145 Denial-of-service (DoS) Vulnerability in Jiffle process (High)
Fixed: GeoServer 2.27.0 | | GeoServer 2.26.3 | GeoServer 2.25.7 -
CVE-2025-27505 Missing Authorization on REST API Index (Moderate)
Fixed: GeoServer 2.26.3 | GeoServer 2.25.6 -
CVE-2024-38524 GWC Home Page exposes sensitive server information (Moderate)
Fixed: GeoServer 2.26.2 | GeoServer 2.25.6 -
CVE-2024-40625 Coverage REST API Server Side Request Forgery (Moderate)
Fixed: GeoServer 2.26.0 -
CVE-2024-29198 Unauthenticated SSRF via TestWfsPost (High)
CVE-2021-40822 SSRF in TestWfsPost for specific targets, e.g. PHP + Nginx (High)
Fixed: GeoServer 2.25.2 | GeoServer 2.24.4This duplication is due to CVE-2021-40822 being generated prior to our use of CVE records.
-
CVE-2024-34711 Improper ENTITY_RESOLUTION_ALLOWLIST URI validation in XML Processing (SSRF) (High)
Fixed: GeoServer 2.25.0
The release announcements listed above have been updated.
Free software is a participation sport - to create a patch for a prior release volunteer with community development.
Q: How often should I upgrade GeoServer?
GeoServer operates with a time boxed release cycle, maintaining “stable” and “maintenance” releases, over the course of a year.
-
Upgrade GeoServer twice a year as new stable releases are made.
-
Once the release you are using has entered “maintenance” it is a good idea to upgrade (before the release is no longer supported).
-
GeoServer security policy provides one year of support. You may also contact our service providers for extended support beyond this timeframe.
Q: Notification of security vulnerabilities?
Stay up to date:
-
Please monitor release announcements for the heading “Security Considerations”.
Security Considerations
This release addresses several security vulnerabilities, and is a recommended upgrade for production systems.
You can review the release announcement, and decide to update.
-
When everyone has had an opportunity to update the details of the vulnerability are announced.
Security Considerations
This release addresses several security vulnerabilities, and is a recommended upgrade for production systems.
- CVE-2024-29198 Unauthenticated SSRF via TestWfsPost (Moderate)
-
Review the full vulnerability to learn more:
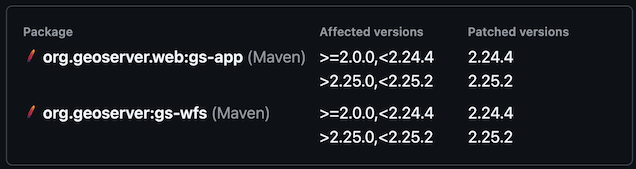
-
Scanning tools also have access to this information when the report is published:
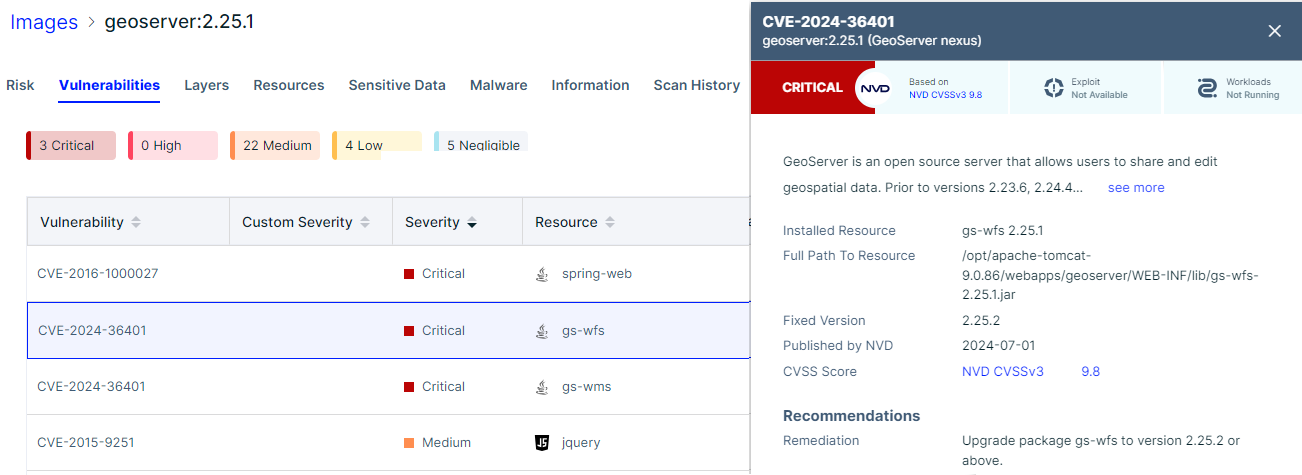
Q: Notification of security reports?
As incoming security reports contain sensitive information they are only shared with representatives of the geoserver-security email list.
Participation in geoserver-security, like commit access, is volunteer based and reflects trust.
Please review GeoServer Security Policy if you are in a position to help out.
Behind The Scenes
- GeoServer 3 First public release date
- GeoServer 3 Sprint Update
- GeoServer 2025 Q4 Developer Update
- GeoServer 3 Crowdfunding Goal Surpassed!
- GeoServer 2025 Q2 Developer Update
- GeoServer 3 Crowdfunding – Last Call!
- GeoServer 3 Crowdfunding Campaign Reaches Major Step: 80% Funding Completion
- GeoServer 2025 Roadmap
- GeoServer 2024 Q4 Developer Update
- GeoServer 3 Call for Crowdfunding