GeoServer Blog
GeoServer 3 Crowdfunding Goal Surpassed!
We are thrilled to announce that the GeoServer 3 crowdfunding campaign has not only met but exceeded its funding target! This remarkable achievement is a testament to the unwavering support and commitment of our global geospatial community.

Why This Matters: GeoServer 3 represents a significant leap forward in open-source geospatial technology. With the funds raised, we will:
- Modernize the platform by upgrading to Spring 6 and JDK 17, ensuring long-term support and compatibility.
- Enhance security through improved authentication mechanisms and compliance with current standards.
- Improve performance by replacing outdated components like JAI with modern alternatives such as ImageN.
- Align with modern deployment environments, facilitating cloud-native and containerized deployments.
Acknowledging Our Community: This milestone was made possible by the collective efforts of individuals, organizations, and institutions worldwide. Your contributions—be it through funding, advocacy, or development—have been instrumental in shaping the future of GeoServer.
Looking Ahead: Surpassing our funding goal allows us to invest additional resources into further enhancements and features, as prioritized by the GeoServer Project Steering Committee (PSC). This includes a stronger focus on security and vulnerability management, ensuring GeoServer remains robust, secure, and resilient in the face of evolving threats. These efforts will help ensure that GeoServer continues to evolve in line with the needs of its diverse user base.
Thank you for being an integral part of this journey. Together, we’ve laid a robust foundation for the next generation of open-source geospatial solutions.
Stay tuned for updates as we embark on this exciting new chapter!
GeoServer 3 is supported by the following organisations:
Individual donations: Abhijit Gujar, Hennessy Becerra, Ivana Ivanova, John Bryant, Jason Horning, Jose Macchi, Peter Smythe, Sajjadul Islam, Sebastiano Meier, Stefan Overkamp.
GeoServer 2.27.1 Release
GeoServer 2.27.1 release is now available with downloads (bin, war, windows), along with docs and extensions.
This is a stable release of GeoServer recommended for production use. GeoServer 2.27.1 is made in conjunction with GeoTools 33.1, and GeoWebCache 1.27.1.
Thanks to Jody Garnett (GeoCat) and Andrea Aime (GeoSolutions) for making this release.
Security Considerations
This release addresses security vulnerabilities and is considered an critical update for production systems.
-
CVE-2025-30220 XML External Entity (XXE) Processing Vulnerability in GeoServer WFS Service (High)
-
CVE-2025-30145 Denial-of-service (DoS) Vulnerability in Jiffle process (High)
See project security policy for more information on how security vulnerabilities are managed.
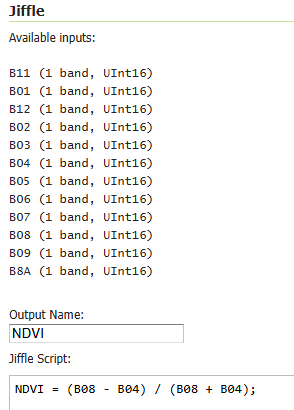
Define Coverage views using Jiffle expressions
A really powerful new features for those working with coverages. You can now create a coverage using the Jiffle “raster calculator” domain specific language.
The use of the CVE system allows the GeoServer team to reach a wider audience than blog posts. For more information please see the user guide. Thanks to Andrea Aime (GeoSolutions) for this new capability.
- GEOS-11797 Add support for Jiffle expressions in coverage view setup
Release notes
New Feature:
- GEOS-11800 Implement GeoServer WPS SpatioTemporalZonalStatistics process
Improvement:
- GEOS-11793 WPS Read Value from Coverage Position
- GEOS-11804 Disallow usage of var in GeoServer source code
Bug:
- GEOS-11274 Cannot get a JSON legend with an external reference to a non published directory
- GEOS-11751 Symbolizer URL in GetLegendGraphic JSON Request is Broken
- GEOS-11795 Incorrect clipping of point geometries in vector tiles
- GEOS-11808 Attribute names containing characters the XML Encoder can’t handle are accepted for input, causing errors
- GEOS-11817 GUI spinner remains after drag and drop
- GEOS-11818 PageUniqueProcess regression after [GEOT-7628]
Task:
- GEOS-11825 Random WPS build failure on Github
- GEOS-11826 Random build failures in gs-metadata when running on Github
- GEOS-11827 Random build failures in LocalResolvetest when running on github actions
- GEOS-11828 Random test failures in WFS 2.0 CITE tests, on Github actions
For the complete list see 2.27.1 release notes.
Community Updates
Community module development:
- GEOS-11816 Features templating OGC API fetch by ID fails
Community modules are shared as source code to encourage collaboration. If a topic being explored is of interest to you, please contact the module developer to offer assistance.
About GeoServer 2.27 Series
Additional information on GeoServer 2.27 series:
GeoServer 2.26.3 Release
GeoServer 2.26.3 release is now available with downloads (bin, war, windows), along with docs and extensions.
This is a maintenance release of GeoServer providing existing installations with minor updates and bug fixes. GeoServer 2.26.3 is made in conjunction with GeoTools 32.3, and GeoWebCache 1.26.3.
Thanks to Jody Garnett and Andrea Aime (GeoSolutions) for making this release.
Security Considerations
This release addresses security vulnerabilities and is considered an critical update for existing installations.
-
CVE-2025-30220 XML External Entity (XXE) Processing Vulnerability in GeoServer WFS Service (High)
-
CVE-2025-30145 Denial-of-service (DoS) Vulnerability in Jiffle process (High)
-
CVE-2025-27505 Missing Authorization on REST API Index (Moderate)
The use of the CVE system allows the GeoServer team to reach a wider audience than blog posts. See project security policy for more information on how security vulnerabilities are managed.
Release notes
New Feature:
- GEOS-11797 Add support for Jiffle expressions in coverage view setup
- GEOS-11800 Implement GeoServer WPS SpatioTemporalZonalStatistics process
Improvement:
- GEOS-11757 Optimize ConfigurationPasswordEncryptionHelper to Cache Encrypted Fields by Store Type
- GEOS-11761 Add support for the clip vendor parameter to WCS as well
- GEOS-11766 Speed up CRS and store factory lookups during catalog loading
- GEOS-11793 WPS Read Value from Coverage Position
- GEOS-11804 Disallow usage of var in GeoServer source code
Bug:
- GEOS-10844 Exclude xml-apis from build
- GEOS-11274 Cannot get a JSON legend with an external reference to a non published directory
- GEOS-11620 Smart Data Loader plugin for GeoServer 2.26 produces a Mapping file data source definition and tries to establish a connection pool, but fails
- GEOS-11664 Update REST security paths
- GEOS-11684 GDAL no longer included in Docker image
- GEOS-11689 IOUtilsTest should not ping an external web site
- GEOS-11690 Bug in Externalize printing configuration folder
- GEOS-11696 AdminRequestCallback not loaded due to spring bean name conflict
- GEOS-11700 GeoFence fails in recognizing some caller IP address
- GEOS-11703 HEAD and OPTIONS requests on the REST API return a 403
- GEOS-11707 Ogr2OgrWfsTest test failures with GDAL 3.10.1
- GEOS-11710 Running Jiffle on coverage views causes the NODATA to be lost
- GEOS-11713 Concurrent LDAP builds fail on Jenkins
- GEOS-11716 WFS POST requests fail if a layer is misconfigured
- GEOS-11720 AttributeTypeInfoImpl doesn’t quote names properly
- GEOS-11722 Coverage view reader partially ignores multithreaded loading
- GEOS-11739 Excessive memory usage for WMS KML output format
- GEOS-11747 GeoServer does not throw JAI runtime exceptions
- GEOS-11751 Symbolizer URL in GetLegendGraphic JSON Request is Broken
- GEOS-11755 AbstractCatalogFacade leaves dangling references to temporary Catalog
- GEOS-11756 GeoServerDataDirectory’s default workspace location is wrong
- GEOS-11760 Fix a potential OOM in the KML transformation
- GEOS-11767 Regression: OL preview always uses JPEG format
- GEOS-11769 Race conditions in LayerGroupHelper when the default catalog is not fully initialized
- GEOS-11774 Logout with OAuth plugin will give error if logged in locally
- GEOS-11776 CVE-2025-27505 Moderate
- GEOS-11792 Default Service Capabilities shown on initial start with no workspaces
- GEOS-11795 Incorrect clipping of point geometries in vector tiles
- GEOS-11818 PageUniqueProcess regression after [GEOT-7628]
Task:
- GEOS-11682 Add tests for WMS SLD XML request reader
- GEOS-11701 Update JAI-Ext to 1.1.28
- GEOS-11743 Upgrade Oracle JDBC driver (ojdbc) from 8 to 11
- GEOS-11763 Update jai-ext to latest version (1.1.30)
- GEOS-11770 Update to jai-ext 1.1.31
- GEOS-11771 Update to Imageio-EXT 1.4.15
- GEOS-11791 Postpone controller logging after data validation
For the complete list see 2.26.3 release notes.
Community Updates
Community module development:
- GEOS-11694 OpenID connect: allow caching authentication when an expiration is declared in the access token
- GEOS-11711 Clickhouse DGGS stores fails to aggregate on dates
- GEOS-11715 STAC sortby won’t work with “properties.” prefixed names
- GEOS-11723 DGGS data store should be able to translate also intersection with multipolygon
- GEOS-11725 Environment parameters resolving is not working on Smart data loader
- GEOS-11738 Prevent error when oidc provider sends empty “&state=”
- GEOS-11741 Enhancing Smart Data Loader with Override Rules
- GEOS-11762 Feature Templates by feature type can not be listed via GeoServer Rest API
- GEOS-11783 Longitudinal profile process should allow for input chaining
- GEOS-11784 The longitudinal profile process should limit the number of points it can extract
- GEOS-11785 The longitudinal profile process should respect cancellation
- GEOS-11786 Longitudinal profile process: general performance improvements
- GEOS-11811 Features templating editor is unable to update and save the template body
Community modules are shared as source code to encourage collaboration. If a topic being explored is of interest to you, please contact the module developer to offer assistance.
About GeoServer 2.26 Series
Additional information on GeoServer 2.26 series:
- GeoServer 2.26 User Manual
- GeoServer 2024 Q3 Developer Update
- Raster Attribute Table extension
- Community module graduation, amending generality rule
- Individual contributor clarification
- Migrate geoserver-users from SourceForge to discourse
Release notes: ( 2.26.3 | 2.26.2 | 2.26.1 | 2.26.0 | 2.26-M0 )
GeoServer 2.25.7 Release
GeoServer 2.25.7 release is now available with downloads (bin, war, windows), along with docs and extensions.
This series has previously reached end-of-life, with this release issued to address an urgent bug or security vulnerability. Please apply this update as a mitigation measure only, and plan to upgrade to a stable or maintenance release of GeoServer. GeoServer 2.25.7 is made in conjunction with GeoTools 31.7.
Thanks to Jody Garnett and Andrea Aime (GeoSolutions) for making this release.
Security Considerations
This release addresses security vulnerabilities and is considered an critical update.
-
CVE-2025-30220 XML External Entity (XXE) Processing Vulnerability in GeoServer WFS Service (High)
-
CVE-2025-30145 Denial-of-service (DoS) Vulnerability in Jiffle process (High)
The use of the CVE system allows the GeoServer team to reach a wider audience than blog posts. See project security policy for more information on how security vulnerabilities are managed.
Release notes
Improvement:
Bug:
- GEOS-11774 Logout with OAuth plugin will give error if logged in locally
Task:
- GEOS-11770 Update to jai-ext 1.1.31
For the complete list see 2.25.7 release notes.
Community Updates
Community module development:
- GEOS-11762 Feature Templates by feature type can not be listed via GeoServer Rest API
- GEOS-11783 Longitudinal profile process should allow for input chaining
- GEOS-11784 The longitudinal profile process should limit the number of points it can extract
- GEOS-11785 The longitudinal profile process should respect cancellation
- GEOS-11786 Longitudinal profile process: general performance improvements
- GEOS-11811 Features templating editor is unable to update and save the template body
Community modules are shared as source code to encourage collaboration. If a topic being explored is of interest to you, please contact the module developer to offer assistance.
About GeoServer 2.25 Series
Additional information on GeoServer 2.25 series:
- GeoServer 2.25 User Manual
- GeoServer 2024 Roadmap Plannings
- Raster Attribute Table extension
- Individual contributor clarification
Release notes: ( 2.25.7 | 2.25.6 | 2.25.5 | 2.25.4 | 2.25.3 | 2.25.2 | 2.25.1 | 2.25.0 | 2.25-RC )
GeoServer 2025 Q2 Developer Update
The GeoServer team is charging ahead with our 2025 roadmap plans.
Thanks to GeoServer 2025 sponsors:
CITE Certification
A great deal of progress has been made on CITE Certification with the most recent GeoServer 2.27.0 Release passing tests! This is great for interoperability and project stability as the CITE tests act as an external “blackbox” testing framework and this verifies that GeoServer is operating as intended.
We are presently determining how to pay for certification:
- The Open Source Geospatial Foundation has negotiated a reduced rate of $150 annual cost per standard certified.
- We are prioritizing tests where we can act as a “reference implementation” resulting in no annual cost for OSGeo.
- For Web Feature Service we pass tests for WFS 2.0, WFS 1.1, and WFS 1.0 which would add up to $450. It may be worthwhile only being certified for the latest WFS 2.0 to reduce the costs to $150.
- There are also now CITE tests for output formats. This would allow the WFS and WPS output to be certified on individual formats like GeoPackage and GeoTIFF.
While GeoServer presently “implements” these standards, our sponsorship level is not sufficient to allow us to feel comfortable paying annual costs for “certification”.
Full certification amounts to $900 a year, while certifying only the latest services amounts to $450 a year.
| OGC Standard | Full Certification | Latest Services | ||
|---|---|---|---|---|
| Services | ||||
| OGC API - Features | $150 | Certified | $150 | Certified |
| WCS 2.0.1 | $0 | Reference | $0 | Reference |
| WCS 1.1.1 | $0 | Reference | $0 | Reference |
| WCS 1.0 | $0 | Reference | $0 | Reference |
| WFS 2.0 | $150 | Certified | $150 | Certified |
| WFS 1.1.0 | $150 | Certified | $0 | Implements |
| WFS 1.0.0 | $0 | Reference | $0 | Reference |
| WMS 1.3.0 | $150 | Certified | $150 | Certified |
| WMS 1.1.1 | $150 | Certified | $0 | Implements |
| WMTS 1.0.0 | $0 | Reference | $0 | Reference |
| Data formats and encodings | ||||
| GeoTIFF 1.1 | $150 | Certified | $0 | Implements |
| GeoPackage 1.2 | $150 | Certified | $0 | Implements |
How you can help: We would really like confirmation that certification is valuable to the community. If you think it is valuable, please let us know in the Discourse forum or, even better, if you are interested in sponsoring part of the certification, please do speak up! If we do not hear from anyone, we might not pursue formal certification any further.
Many thanks to prior sponsors of this activity including Gaia3D, and OSGeo:UK.
GeoServer 3
The big news is that GeoServer 3 crowdfunding campaign phase one has been successful, allowing the project plan milestones to be scheduled.
We are working around the GeoServer release schedule to avoid disruption to the project:
-
Milestone 1 : Preparation (May-September)
Doing everything possible ahead of time before the migration to spring-framework-6.Milestone 1 is already in progress, see the headings below for specific activities.
Milestone 1 activities will be taking place on the
mainbranch ahead of the GeoServer 2.28 release. As tasks are completed, your feedback and continuous testing of nightly builds will be highly appreciated. Please chat to us about how you can automate the testing in your non-production environments. -
Milestone 2 : Migration (October-December)
Requires a coordinated “code-freeze” across nine codebases migrating to spring-framework-6.This activity is going to take careful planning, and we anticipate scheduling an in-person sprint for the migration.
While initial work may occur on a
devbranch, GeoServer 3 will take over themainbranch after the September release of GeoServer 2.28.0. -
Milestone 3: Delivery (January-March)
The moment we have the code-base working again, Milestone 3 activities include continuing the testing of nightly builds, checking integration with downstream applications, and feedback from anyone wishing to work on restoring a community module to GeoServer 3.This pace allows GeoServer 3.0 to be ready in 2026 Q1, respecting our normal time-boxed release cycle.
Milestone 1
Checking in on Milestone 1 activities, there is lots of work to be done!
Spring Framework Preparation, Java 17, and Project and Build Support
To get the codebase ready for widespread change, Gabriel will be looking at setting up a GeoTools “bill of materials” pom.xml file providing GeoServer and other applications an easy way to manage the currently tested set of dependencies.
- Updating to Java 17 is a key requirement for Spring Framework 6 and JakartaEE so expect many of these dependencies to be updated or replaced over the course of GeoServer 2.28 development.
- Spring Framework 6 also removes a lot of deprecated APIs and dependencies, providing work to do for GeoWebCache and GeoServer codebases
ImageN and JAI-Ext Online Sprint (May 26-27)
The biggest GeoServer 3 Milestone 1 activity is restarting the ImageN project and combining forces with JAI-Ext for a new image processing engine:
- ImageN represents the Oracle donation of the original Java Advanced Imaging codebase to the Eclipse Foundation (using a new name that does not contain “Java”).
- The ImageN project is being restarted, with Andrea and Daniele being recently added to the project.
- Project website has been updated with a slightly revised scope to reflect the addition of the JAI-Ext codebase.
- We will be cutting some unused functionality, such as RMI, and restructuring the maven build to reflect some of the lessons learned with JAI-Ext and GeoTools build practices.
- Andrea has a rough project plan which we will capture as a project board in the weeks ahead.
- Communication is taking place over on the imagen-dev mailing list.
Andrea and Jody are organizing an ImageN Online Sprint for May 26-27 where the bulk of the work will take place. We plan to follow the same approach as the OpenGIS Harmonization activity where refactor scripts are produced, and tested on the GeoTools / GeoWebCache / GeoServer codebases during development.
Spring Security and OAuth2 / OIDC Security Modules
The next technical challenge is the work needed to update to the next version (6) of the Spring Security Framework. There have been considerable API changes, resulting in the need to completely replace the existing OAuth2 and OIDC community modules. Our existing community modules are based on the deprecated spring-security-oauth library which has now reached end of life. The Spring Security Core library now has OAuth2 support, necessitating a new GeoServer extension that makes direct use of the built-in OAuth2 support.
Andreas Watermeyer (ITS Digital Solutions) has working on these activities:
- GeoServer 2.27.0 includes the upgrade to Spring Security 5.8, and there is a checklist to complete before upgrading further to version 6.
- Andreas has a draft pull request re-implementing the OAuth2 security modules, which we are looking forward to incorporating, and we plan to port all the test cases over to ensure that it covers the same functionality.
Ideally GeoServer 2.28.0 will include both the old and the new Spring Security OAuth2 community modules, allowing everyone to upgrade easily and report back any regressions found.
Wicket
A big accomplishment in the recent GeoServer 2.27.0 Release is progress towards Wicket 10 by Brad and David:
- Wicket 9
- Wicket Dialog
- Wicket Content Security Policy
There are a few remaining items to work on, such as the Java 17 build, before upgrading to Wicket 10.
It is great that we have already tackled many of the technical challenges above, and have received positive responses from GeoServer 2.27.0 testers.
Crowdfunding
GeoServer 3 crowdfunding has completed the Commitment Phase - thank you for your trust and support. We are now contacting supporters to engage with them further.
GeoServer 3 is supported by the following organisations:
Individual donations: Abhijit Gujar, Hennessy Becerra, Ivana Ivanova, John Bryant, Jason Horning, Jose Macchi, Peter Smythe, Sajjadul Islam, Sebastiano Meier, Stefan Overkamp.
Behind The Scenes
- GeoServer 3 First public release date
- GeoServer 3 Sprint Update
- GeoServer 2025 Q4 Developer Update
- GeoServer 3 Crowdfunding Goal Surpassed!
- GeoServer 2025 Q2 Developer Update
- GeoServer 3 Crowdfunding – Last Call!
- GeoServer 3 Crowdfunding Campaign Reaches Major Step: 80% Funding Completion
- GeoServer 2025 Roadmap
- GeoServer 2024 Q4 Developer Update
- GeoServer 3 Call for Crowdfunding