GeoServer Blog
OGC Filter Injection Vulnerability Statement
A vulnerability has located in the GeoTools Library that allows SQL Injection using OGC Filter and Function expressions.
- CVE-2023-25157 OGC Filter SQL Injection Vulnerabilities (GeoServer)
- CVE-2023-25158 OGC Filter SQL Injection Vulnerabilities (GeoTools)
If you wish to report a security vulnerability, see instructions on responsible reporting. We also welcome your direct financial support.
Assessment
SQL Injection Vulnerabilities have been found with:
PropertyIsLikefilter, when used with a String field and any relational database based Store, or with a PostGIS DataStore with encode functions enabled, or with any image mosaic with an index stored in a relational database.strEndsWithfunction, when used with a PostGIS DataStore with encode functions enabledstrStartsWithfunction, when used with a PostGIS DataStore with encode functions enabledFeatureIdfilter, when used with any database table having a String primary key column and when prepared statements are disabledjsonArrayContainsfunction, when used with a String or JSON field and with a PostGIS or Oracle DataStore (GeoServer 2.22.0+ only)DWithinfilter, when used with an Oracle DataStore
Mitigation
We recommend upgrading. The following list of mitigations is addressing some of the issues (e.g., the PropertyIsLike issue has no mitigation for tables with a string field):
- Disabling the PostGIS Datastore encode functions setting to mitigate
strEndsWith,strStartsWith(will cause severe slowdowns in parts of the WMTS multidimensional plugin functionality, if in use). - Enabling the PostGIS DataStore preparedStatements setting to mitigate the
FeatureIdvulnerability. - No mitigation is available for
PropertyIsLikefilter, you may choose to disable database DataStores until you are able to upgrade. - No mitigation is available for
DWithinwith Oracle DataStore, you may choose to disable Oracle DataStores until you are able to upgrade. - As a good practice to limit the attack surface, it’s important to give the database account used for connection pools the minimum required level of privileges (e.g., read-only unless WFS-T/importer/REST granule harvesting are used, access limited only to the schemas and tables needed for production usage)
Resolution
Issues:
- GEOT-7302 Escape user inputs in SQL queries
- GEOS-10842 Escape user inputs in SQL queries
-
GEOS-10839 Add JDBC Configuration parameter to disable SQL comments and pretty-printing
A related issue with the community jdbc-config module.
Patched releases:
- GeoServer 2.23.0 scheduled release
- GeoServer 2.22.2 stable release
- GeoServer 2.21.4 maintenance
- GeoServer 2.20.7
- GeoServer 2.19.7
- GeoServer 2.18.7
If you wish to volunteer to backport these fixes to other GeoServer series and make a release co-ordinate on the developers list. If you are not in a position to collaborate reach out to a commercial support provider to act on your behalf.
Thanks to Steve Ikeoka for responsibly reporting and fixing these issues. Thanks to Jody Garnett (GeoCat) for the stable and maintenance releases. Thanks to Andrea Aime (GeoSolutions) for back porting this fix to versions of GeoTools and GeoServer that are otherwise no longer receiving releases.
GeoServer 2.22.2 Release
GeoServer 2.22.2 release is now available with downloads (bin, war, windows), along with docs and extensions.
This is a stable release of the GeoServer 2.22.x series, made in conjunction with GeoTools 28.2 and GeoWebCache 1.22.1.
This release was scheduled early to address a security vulnerability. Thanks to Jody Garnett for making this release on behalf of GeoCat Live.
Security Considerations
This release addresses a security vulnerability and is considered an essential upgrade for production systems:
- CVE-2023-25158 OGC Filter SQL Injection Vulnerabilities (GeoTools)
- CVE-2023-25157 OGC Filter SQL Injection Vulnerabilities (GeoServer)
For more information see OGC Filter Injection Vulnerability Statement.
- GEOT-7302 Escape user inputs in SQL queries
- GEOS-10842 JDBCConfig: escape user inputs in SQL queries
- GEOS-10839 JDBCConfig: add JDBC Configuration parameter to disable SQL comments and pretty-printing
2024-06-30 Update: The following mitigation has been provided:
-
CVE-2024-36401 Remote Code Execution (RCE) vulnerability in evaluating property name expressions (Critical)
geoserver-2.22.2-patches.zip (replacing
gt-app-schema,gt-complexandgt-xsd-corejars) has been provided by Andrea (GeoSolutions)
See project security policy for more information on how security vulnerabilities are managed.
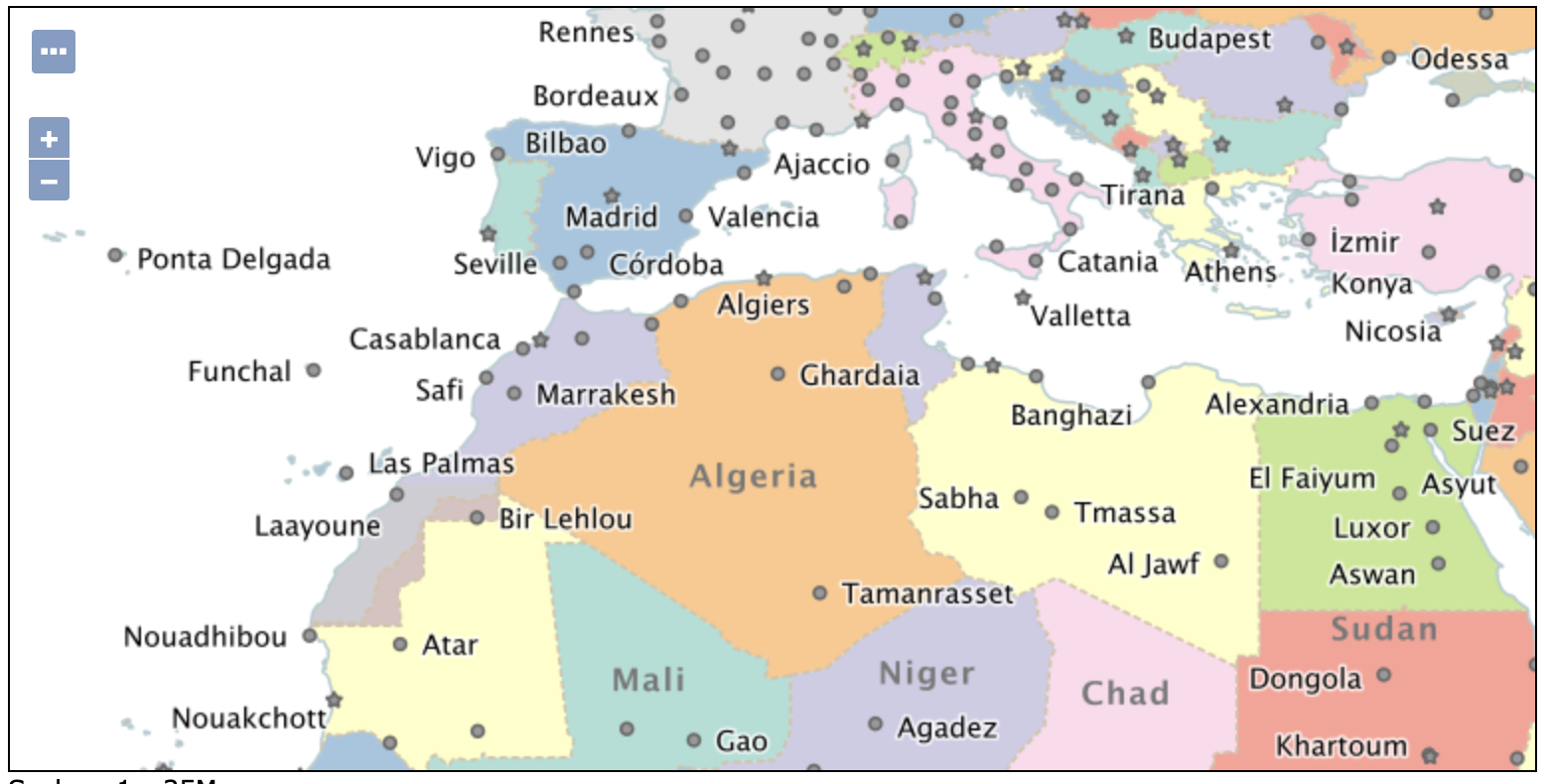
Natural Earth 50m Sample Data
The Natural Earth ne workspace has been improved with 1:50m sample data offering the following:
- improved detail
- country labels in multiple languages
- disputed regions
The countries.sld style includes the following:
<sld:TextSymbolizer>
<sld:Label>
<ogc:Function name="Recode">
<ogc:Function name="language"/>
<ogc:Literal/>
<ogc:PropertyName>NAME</ogc:PropertyName>
<ogc:Literal>en</ogc:Literal>
<ogc:PropertyName>NAME</ogc:PropertyName>
<ogc:Literal>it</ogc:Literal>
<ogc:PropertyName>NAME_IT</ogc:PropertyName>
<ogc:Literal>fr</ogc:Literal>
<ogc:PropertyName>NAME_FR</ogc:PropertyName>
</ogc:Function>
</sld:Label>
To try this out in French append &LANGUAGE=fr to any GetMap request, including Layer Preview.
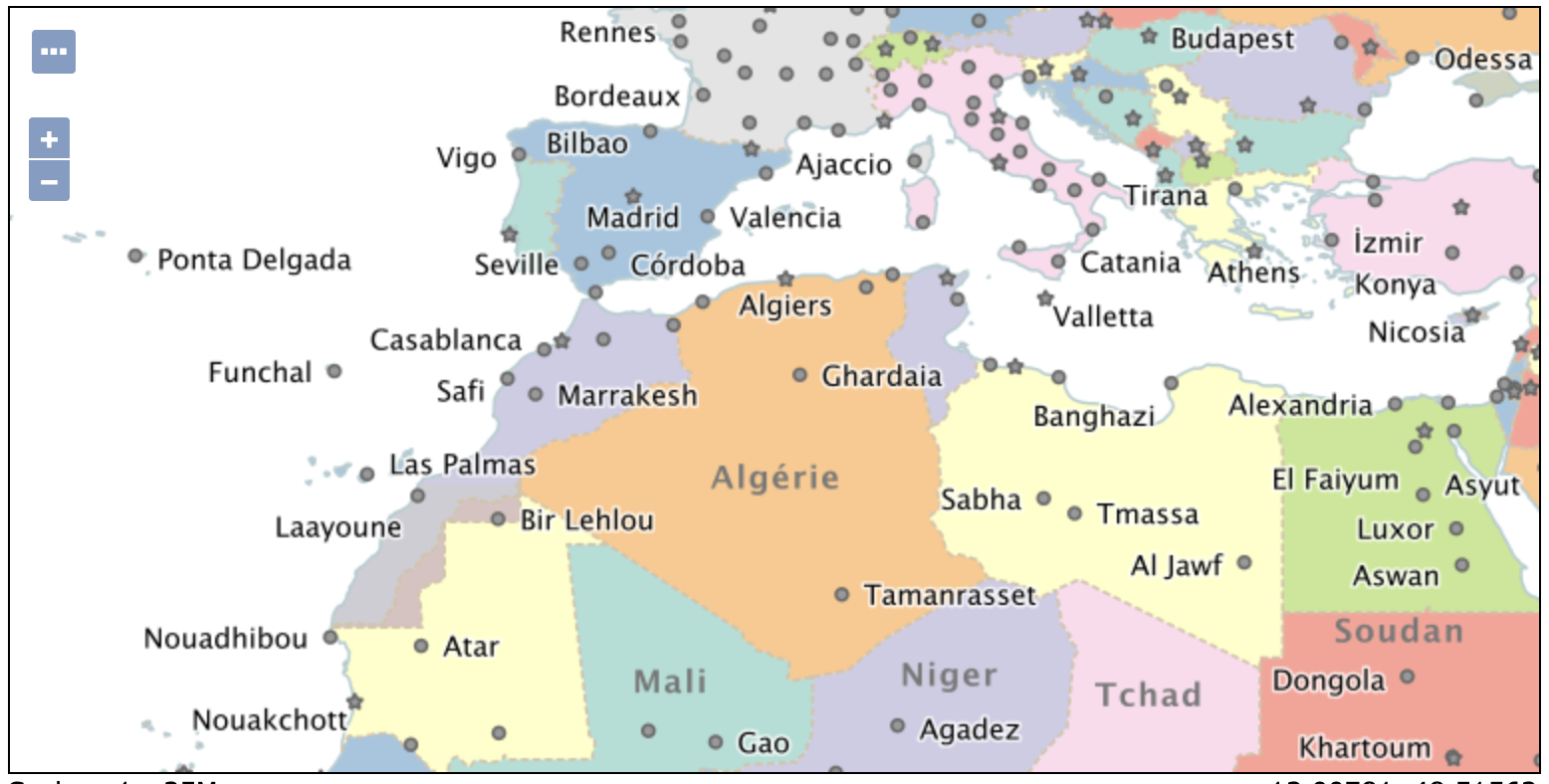
These styles also now validate. Thanks to Jody Garnett (GeoCat) for this work.
- GEOS-10624 Data directory and documentation update
- GEOS-10836 The demo styles in “ne” workspace do not validate
Welcome Page Performance Improvements
The welcome page loading is now limited to a short amount of time to retrieve the list of workspaces and layers to select from. For large catalogues, with lots of security restrictions, that are unable to respond in this time, a simple text field is provided.
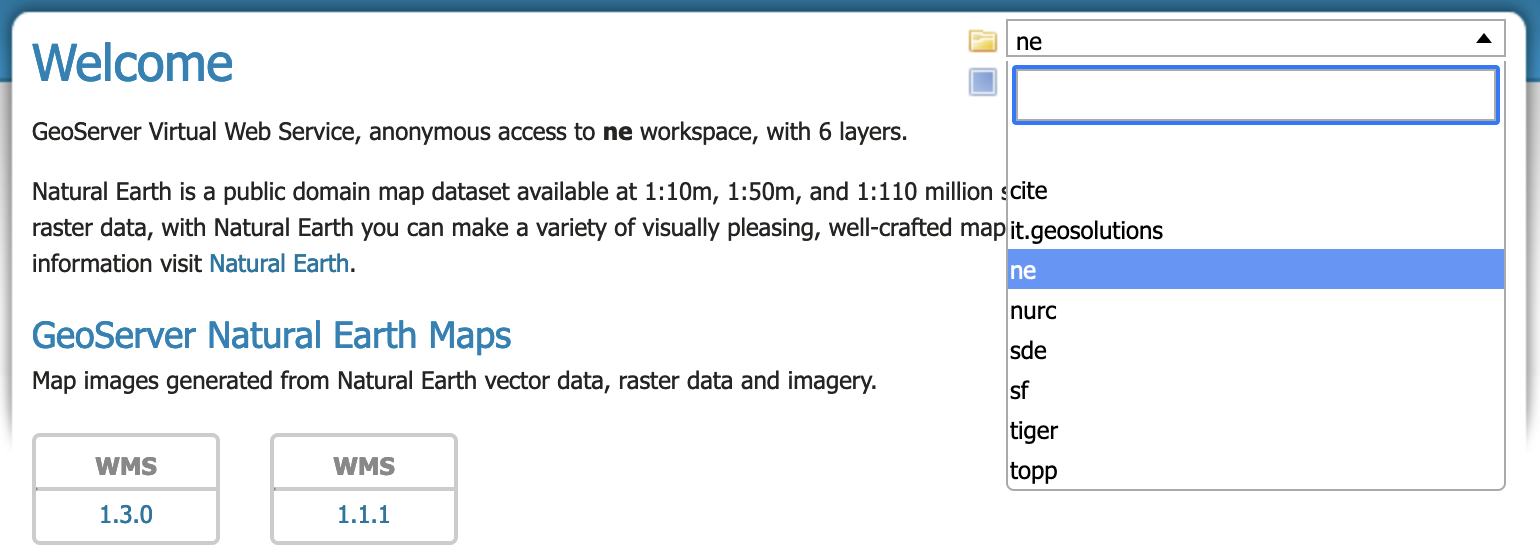
To force the use of a simple text field the property GeoServerHomePage.selectionMode=TEXT can be used. Use DROPDOWN to force a selection control to be used, or AUTOMATIC to determine the behaviour based on catalogue performance as described above.
The default time out GeoServerHomePage.selectionTimeout=5000 for interaction can be adjusted if you would like to provide the catalogue more time to respond.
By default GeoServerHomePage.selectionMaxItems=1000 workspaces or layers can be loaded. This number may be limited further if you find browser performance is affected.
Thanks to Andrea (GeoSolutions) for these performance improvements, and Jody Garnett for a number of smaller fixes.
-
GEOS-10833 GeoServerHomePage unresponsive against large catalogs
-
GEOS-10759 Welcome page unreachable with large / slow catalogue configuration
-
GEOS-10838 Speed up DefaultResourceAccessManager securityFilter implementation
-
GEOS-10834 Catalog.list might require a lot of time due to security filtering
-
GEOS-10847 Selecting a raster layer in home page shows incorrect services
-
GEOS-10861 Welcome blurb i18n not respecting language switch
Community Modules
OGC API updates:
-
GEOS-10860 OGC API should return version including minor and patch in HTTP Response Header
-
GEOS-10828 OGC API - Features - Plugin breaks core `/rest` API with JSON payloads
The JDBC Config module received several important fixes:
-
GEOS-10814 Update jdbc config to use consistent SQL formatting
-
GEOS-10813 jdbc config cache bug
-
GEOS-10829 JDBC Config missing some nested layer properties
-
GEOS-10842 Escape user inputs in SQL queries
Release notes
Improvement:
- GEOS-10851 GWC S3 Blobstore Parameters Get Converted back to plain text after an application restart
Bug:
-
GEOS-7506 shutdown.bat cannot run without JAVA_HOME set
-
GEOS-10689 OSHISystemInfoCollector holds non daemon threads, prevents clean shutdown of Tomcat
-
GEOS-10846 Enable auto-escaping for REST HTML templates
Task:
-
GEOS-10683 FileWrapperResourceTheoryTest fails on Windows since Java 11
-
GEOS-10848 Column remarks documentation should be updated to reflect that functionality is supported with JNDI
For complete information see 2.22.2 release notes.
About GeoServer 2.22
Additional information on GeoServer 2.22 series:
- Update Instructions
- Metadata extension
- CSW ISO Metadata extension
- State of GeoServer (FOSS4G Presentation)
- GeoServer Beginner Workshop (FOSS4G Workshop)
- Welcome page (User Guide)
Release notes: ( 2.22.2 | 2.22.1 | 2.22.0 | 2.22-RC | 2.22-M0 )
GeoServer 2.21.4 Release
GeoServer 2.21.4 release is now available with downloads (bin, war, windows), along with docs and extensions.
This is a maintenance release of the GeoServer 2.21.x series, made in conjunction with GeoTools 27.4 and GeoWebCache 1.21.4.
Thanks to Jody Garnett (GeoCat) for making this release.
Security Considerations
This release addresses a security vulnerability and is considered an essential upgrade for production systems:
- CVE-2023-25158 OGC Filter SQL Injection Vulnerabilities (GeoTools)
- CVE-2023-25157 OGC Filter SQL Injection Vulnerabilities (GeoServer)
For more information see OGC Filter Injection Vulnerability Statement.
- GEOT-7302 Escape user inputs in SQL queries
- GEOS-10842 JDBCConfig: escape user inputs in SQL queries
- GEOS-10839 JDBCConfig: add JDBC Configuration parameter to disable SQL comments and pretty-printing
2024-06-30 Update: The following mitigation has been provided:
-
CVE-2024-36401 Remote Code Execution (RCE) vulnerability in evaluating property name expressions (Critical)
geoserver-2.21.4-patches.zip (replacing
gt-app-schema,gt-complexandgt-xsd-corejars) has been provided by Andrea (GeoSolutions)
See project security policy for more information on how security vulnerabilities are managed.
Community Modules
The JDBC Config module received several important fixes:
-
GEOS-10814 Update jdbc config to use consistent SQL formatting
-
GEOS-10813 jdbc config cache bug
-
GEOS-10829 JDBC Config missing some nested layer properties
-
GEOS-10842 JDBCConfig: escape user inputs in SQL queries
Release notes
Bug:
-
GEOS-7506 shutdown.bat cannot run without JAVA_HOME set
-
GEOS-10683 FileWrapperResourceTheoryTest fails on Windows since Java 11
-
GEOS-10689 OSHISystemInfoCollector holds non daemon threads, prevents clean shutdown of Tomcat
-
GEOS-10807 LayerGroup with nested group POST rest op fails with null styles attribute
-
GEOS-10817 Features Templating - XML HTML output doesn’t escape all html and xml symbols
-
GEOS-10818 Schemaless Property Accessor returns emptylist instead of null for null/not existing properties
-
GEOS-10846 Enable auto-escaping for REST HTML templates
Improvement:
-
GEOS-10816 OGC API Features complex features test fails since introduction of tag in HTML templates
-
GEOS-10848 Column remarks documentation should be updated to reflect that functionality is supported with JNDI
-
GEOS-10851 GWC S3 Blobstore Parameters Get Converted back to plain text after an application restart
For complete information see 2.21.4 release notes.
About GeoServer 2.21
Additional information on GeoServer 2.21 series:
Release notes: ( 2.21.4 | 2.21.3 | 2.21.2 | 2.21.1 | 2.21.0 | 2.21-RC )
GeoServer 2.20.7 Released
GeoServer 2.20.7 release is available with downloads (bin, war, windows), along with docs and extensions.
This series has previously reached end-of-life, with a release being issued to address an urdent security vulnerability. Please apply this upgrade as a mitigation measure only. Upgrade to 2.22.x series for community support.
Thanks to Andrea Aime (GeoSolutions) for making this update available on behalf of the GeoNode project.
This release was made in conjunction with GeoTools 26.7.
Security Considerations
This release addresses a security vulnerability and is considered an essential upgrade for production systems:
- CVE-2023-25158 OGC Filter SQL Injection Vulnerabilities (GeoTools)
- CVE-2023-25157 OGC Filter SQL Injection Vulnerabilities (GeoServer)
For more information see OGC Filter Injection Vulnerability Statement.
- GEOT-7302 Escape user inputs in SQL queries
- GEOS-10842 JDBCConfig: escape user inputs in SQL queries
- GEOS-10839 JDBCConfig: add JDBC Configuration parameter to disable SQL comments and pretty-printing
2024-06-30 Update: The following mitigation has been provided:
-
CVE-2024-36401 Remote Code Execution (RCE) vulnerability in evaluating property name expressions (Critical)
geoserver-2.20.7-patches.zip (replacing
gt-app-schema,gt-complexandgt-xsd-corejars) has been provided by Andrea (GeoSolutions)
See project security policy for more information on how security vulnerabilities are managed.
Improvements and Fixes
For the full list of fixes and improvements, see 2.20.7 release notes.
About GeoServer 2.20
Additional information on GeoServer 2.20 series:
- Log4J2 zero day vulnerability assessment
- Internationalization of title and abstract
- State of GeoServer 2.20 edition
- Windows Installer
Release notes: ( 2.20.7 | 2.20.6 | 2.20.5 | 2.20.4 | 2.20.3 | 2.20.2 | 2.20.1 | 2.20.0 | 2.20-RC )
GeoServer 2.19.7 Released
GeoServer 2.19.7 release is now available with downloads (bin, war, windows), along with docs and extensions.
This series has previously reached end-of-life, with an extra maintenance release being issued to address an urgent security vulnerability. Please apply this upgrade as a mitigation measure only. Upgrade to 2.22.x series for community support.
Thanks to Andrea Aime (GeoSolutions) for making this update available on behalf of GeoSolutions customers.
This release was made in conjunction with GeoTools 25.7.
Security Considerations
This release addresses a security vulnerability and is considered an essential upgrade for production systems:
- CVE-2023-25158 OGC Filter SQL Injection Vulnerabilities (GeoTools)
- CVE-2023-25157 OGC Filter SQL Injection Vulnerabilities (GeoServer)
For more information see OGC Filter Injection Vulnerability Statement.
- GEOT-7302 Escape user inputs in SQL queries
- GEOS-10842 JDBCConfig: escape user inputs in SQL queries
- GEOS-10839 JDBCConfig: add JDBC Configuration parameter to disable SQL comments and pretty-printing
Improvements and Fixes
For more information see 2.19.7 release notes.
About GeoServer 2.19
Additional information on GeoServer 2.19 series:
- Jiffle and GeoTools RCE vulnerabilities
- Log4J2 zero day vulnerability assessment
- WMS GetFeatureInfo includes labels from ColorMap
- Promote WMTS multidim to extension
- Promote WPS-Download to extension
- Promote params-extractor to extension
- Promote GWC-S3 to extension
- Promote WPS-JDBC to extension status
- Promote MapML to extension status
- GeoServer repository transition to main branch
Release notes ( 2.19.7 | 2.19.6 | 2.19.5 | 2.19.4 | 2.19.3 | 2.19.2 | 2.19.1 | 2.19.0 | 2.19-RC )