GeoServer Blog
Powerful SLD Styles & Filters in GeoServer
GeoSpatial Techno is a startup focused on geospatial information that is providing e-learning courses to enhance the knowledge of geospatial information users, students, and other startups. The main approach of this startup is providing quality, valid specialized training in the field of geospatial information.
( YouTube | LinkedIn | Facebook | X )
Powerful SLD Styles and Filters in GeoServer
In this session, we’ll explore GeoServer SLD styles and filters and highlight their practical and versatile uses. If you want to access the complete tutorial, click on the link.
Introduction
Filters in GeoServer are essential for controlling map data display, allowing users to set conditions for data inclusion. By integrating these filters into a Styled Layer Descriptor (SLD), users can customize maps based on specific attribute values or spatial areas. This customization enables the creation of visually informative and meaningful maps that effectively showcase data.
Several types of filters can be used in GeoServer styling, such as Comparison operators , Spatial operators , Logical operators and Arithmetic operators.
Note. This video was recorded on GeoServer 2.22.4, which is not the most up-to-date version. We encourage all users to use the stable series, currently 2.28.x. To ensure you have the latest release, please visit this link and avoid using older versions of GeoServer.
Note. In all examples in this blog post, we utilize the topp:states layer.
Comparison Operators
These operators allow users to filter data by focusing on non-spatial attributes of a feature, selecting specific values within a field, or defining a range of values. This functionality helps refine search results within a dataset for more precise data analysis.
The Comparison operators include: Binary comparison operators and Value comparison operators.
The binary comparison operators are: PropertyIsEqualTo , PropertyIsNotEqualTo , PropertyIsLessThan , PropertyIsLessThanOrEqualTo , PropertyIsGreaterThan and PropertyIsGreaterThanOrEqualTo.
To learn how to use various filters for creating a custom SLD style in GeoServer, follow these steps:
- Navigate to the Styles page from the Data section, then click on Add a new style link.
- In the Name field, type your desired name, such as
Comparison_lessThan. - Select Polygon from the list of default styles, then click the Generate link.
-
Type the new title on line 13, and press the ‘Enter’ key at the end of the line. Then, add the following block codes to the new line:
<ogc:Filter> <ogc:PropertyIsLessThan> <ogc:PropertyName>PERSONS</ogc:PropertyName> <ogc:Literal>1000000</ogc:Literal> </ogc:PropertyIsLessThan> </ogc:Filter> - Press the Validate button to check if you have misspelled anything. If there are no errors, press the Apply button.
- Switch to the Layer Preview tab and click the layer name above the preview box and select
topp:stateslayer.
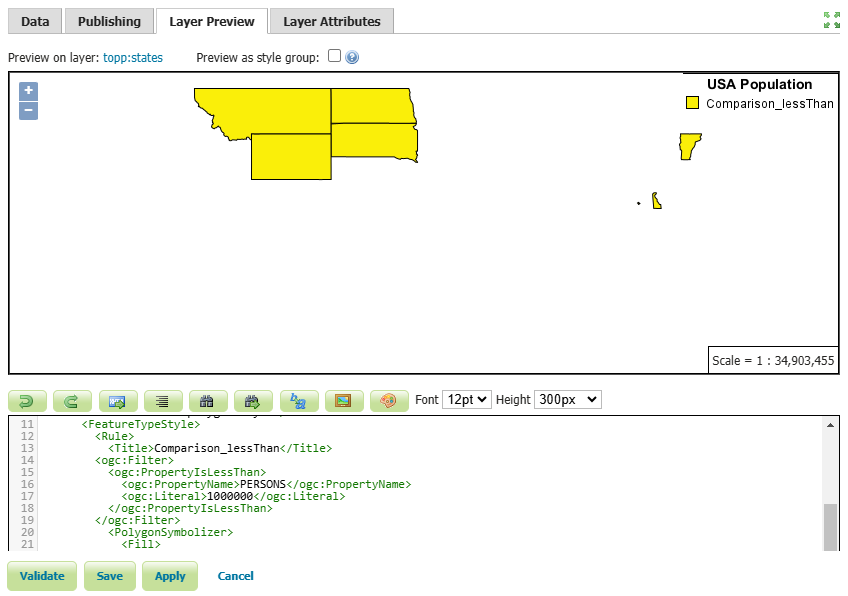 In this example, we have created a style for states with a population of less than one million.
In this example, we have created a style for states with a population of less than one million.
- Press the Save button.
Other available comparison operators, known as the value comparison operators include: PropertyIsLike , PropertyIsNull, and PropertyIsBetween.
To use the PropertyIsLike operator in a new style, follow these steps:
-
Click on Add a new style link, then enter
Comparison_likein the Name field. -
Select Comparison_lessThan from the existing styles, then click the Copy link.
-
To filter the states that include
newin their name, modify the existing codes using the following codes:<ogc:Filter> <ogc:PropertyIsLike wildCard="%" singleChar="_" escape="!"> <ogc:PropertyName>STATE_NAME</ogc:PropertyName> <ogc:Literal>%new%</ogc:Literal> </ogc:PropertyIsLike> </ogc:Filter> -
Additionally, insert the following block of code on line 30 to display the names of the states as well.
<TextSymbolizer> <Label> <ogc:PropertyName>STATE_NAME</ogc:PropertyName> </Label> <VendorOption name="maxDisplacement">50</VendorOption> </TextSymbolizer> -
Press the Validate button to check if you have misspelled anything. If there are no errors, press the Apply button.
-
Switch to the Layer Preview tab and click the layer name above the preview box and select
topp:stateslayer.
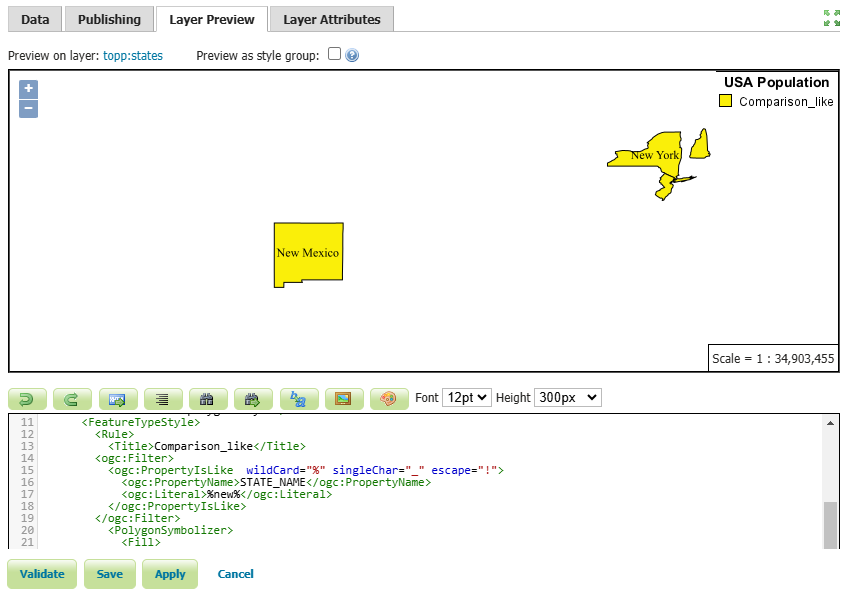
In this example, we filtered the states that have the word new in their name, such as: New York , New Jersey , New Hampshire and New Mexico.
- Press the Save button.
Spatial Operators
These operators allow users to filter data based on its spatial location. This can include filtering data based on its proximity to a specific point, within a specific area or boundary, or in relation to other spatial features.
Some common spatial operators include: Within , Contains , Intersects , BBOX , etc. For a comprehensive list of all the spatial operators, please visit this link
Follow these steps to use the Intersects filter in a new style:
- Click on Add a new style link, then enter
spatial_intersectsin the Name field. - Select
comparison_likefrom the existing styles, then click the Copy link. -
Edit the codes using the following codes:
<ogc:Filter xmlns:gml="http://www.opengis.net/gml"> <ogc:Intersects> <ogc:PropertyName>the_geom</ogc:PropertyName> <gml:LineString> <gml:coordinates>-112.5,34.7 -106.8,36.7 -100.5,36.8 -97.4,42.4</gml:coordinates> </gml:LineString> </ogc:Intersects> </ogc:Filter> - Press the Validate button to check if you have misspelled anything. If there are no errors, press the Apply button.
- Switch to the Layer Preview tab and select
topp:stateslayer.
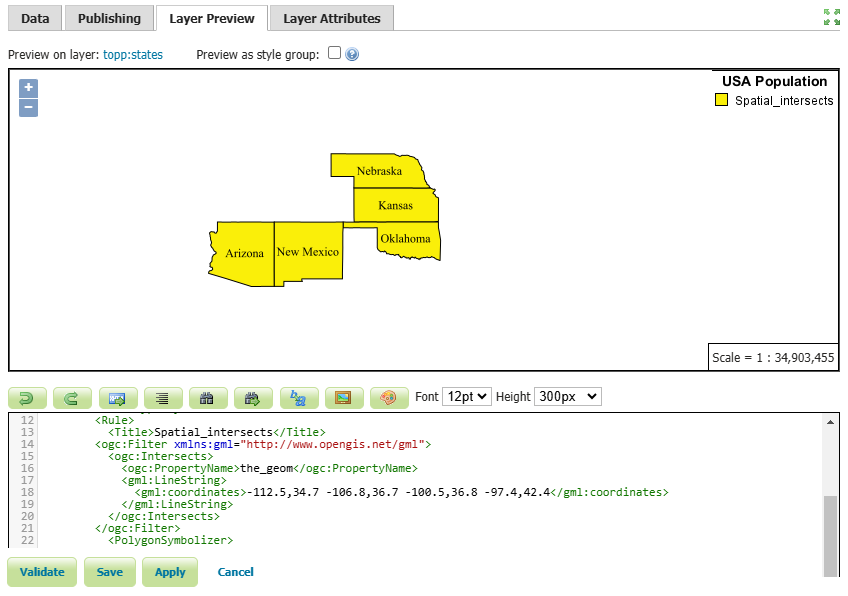
The states that intersect with a LineString, determined by the specified coordinates, include Arizona, New Mexico, Oklahoma, Kansas and Nebraska.
- Press the Save button.
Logical Operators
Logical operators are used to set conditions for applying specific style rules to features. They allow users to create complex rules based on various attributes and conditions. In GeoServer, the key logical operators are AND, OR, and NOT.
- AND: Both specified conditions must be true for the style rule to be applied.
- OR: At least one of the specified conditions must be true for the style rule to be applied.
- NOT: The style rule will not apply to features that do not meet the specified condition.
Here’s an example of how to use the AND operator to filter a SLD based on two conditions.
-
Click on Add a new style link, then enter
logical_andin the Name field. -
Select
spatial_intersectsfrom the existing styles, then click the Copy link. -
Edit the codes using the block codes below:
<ogc:Filter xmlns:gml="http://www.opengis.net/gml"> <ogc:And> <ogc:BBOX> <ogc:PropertyName>the_geom</ogc:PropertyName> <gml:Box> <gml:coord> <gml:X>-105</gml:X> <gml:Y>35</gml:Y> </gml:coord> <gml:coord> <gml:X>-90</gml:X> <gml:Y>45</gml:Y> </gml:coord> </gml:Box> </ogc:BBOX> <ogc:PropertyIsBetween> <ogc:PropertyName>PERSONS</ogc:PropertyName> <ogc:LowerBoundary> <ogc:Literal>3000000</ogc:Literal> </ogc:LowerBoundary> <ogc:UpperBoundary> <ogc:Literal>5000000</ogc:Literal> </ogc:UpperBoundary> </ogc:PropertyIsBetween> </ogc:And> </ogc:Filter> - Press the Validate button to check if you have misspelled anything. If there are no errors, press the Apply button.
- Switch to the Layer Preview tab and select
topp:stateslayer.
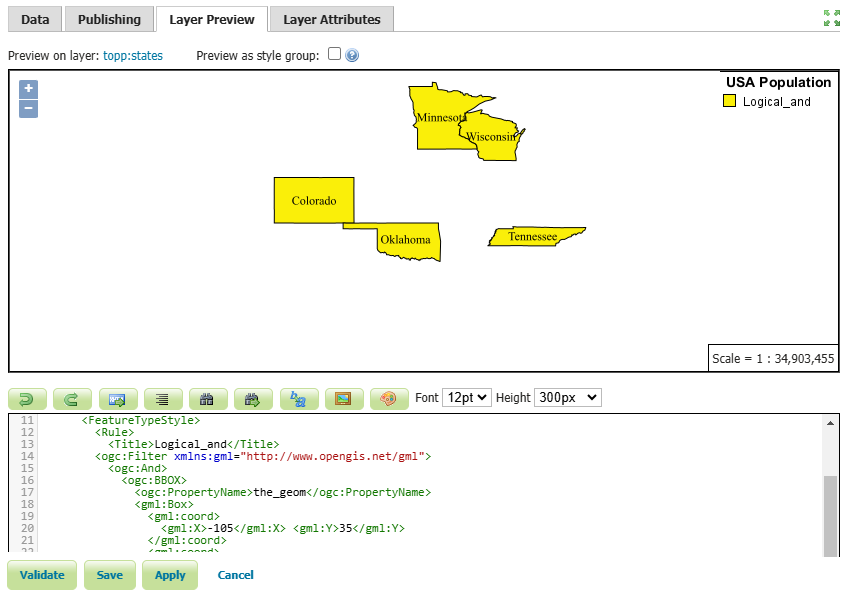
In this example, the states that intersect a certain bounding box and have a population between 3 million and 5 million have been filtered. The states that meet these criteria are Colorado, Oklahoma, Tennessee, Minnesota and Wisconsin.
- Press the Save button.
Arithmetic operators
Arithmetic operators enable users to create custom visualizations through mathematical equations and expressions, allowing them to effectively convey their data visually on maps.
The available arithmetic operators include: Add , Sub , Mul and Div.
For example, you can use arithmetic operators to create a proportional symbol map, where the size of point symbols is based on a numeric attribute value. By dividing the attribute value by a constant factor, you can control the size of the symbols accordingly.
Here’s an example of how to use this operator in GeoServer:
-
Click on Add a new style link, then enter
arithmetic_divin the Name field. -
Select Polygon from the list of default styles, then click the Generate link.
-
Enter the following code snippet on line 26:
<Rule> <Name/> <Title>PERSONS Symbol</Title> <PointSymbolizer> <Geometry> <ogc:Function name="centroid"> <ogc:PropertyName>the_geom</ogc:PropertyName> </ogc:Function> </Geometry> <Graphic> <Mark> <WellKnownName>circle</WellKnownName> <Fill> <CssParameter name="fill">#FF0000</CssParameter> </Fill> <Stroke> <CssParameter name="stroke">#000000</CssParameter> <CssParameter name="stroke-width">1</CssParameter> </Stroke> </Mark> <Size> <ogc:Div> <ogc:PropertyName>PERSONS</ogc:PropertyName> <ogc:Literal>1000000</ogc:Literal> </ogc:Div> </Size> </Graphic> </PointSymbolizer> </Rule>
In this example, we have defined two rules. The first rule is to display the simple polygons representing the states, while the second rule is to create circular symbols based on the population of each state.
We used the Centroid function to assign a symbol to each state, and place it exactly in the center of each polygon. In addition, we divided the Persons attribute by one million to ensure a proportional representation of the symbol size to the polygons.
-
Press the Validate button to check if you have misspelled anything. If there are no errors, press the Apply button.
-
Switch to the Layer Preview tab and select
topp:stateslayer.
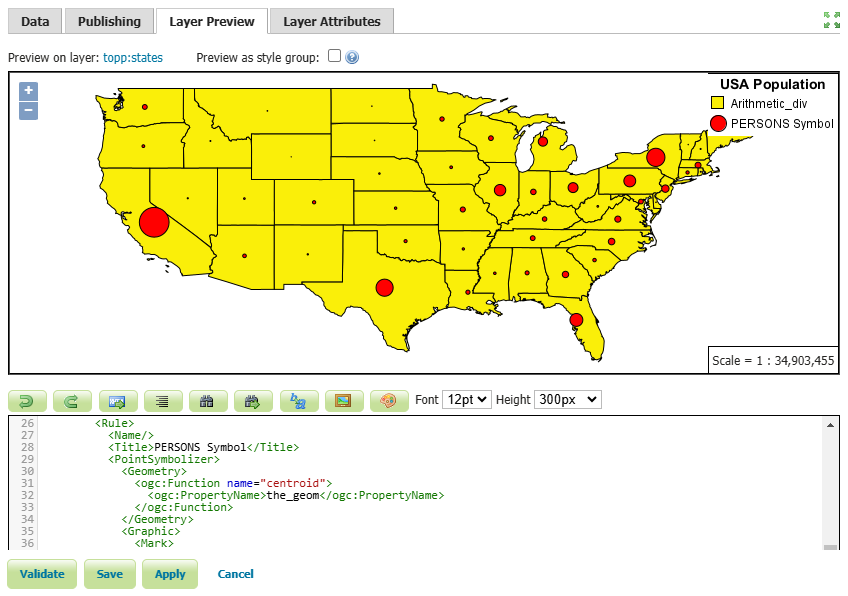
As you can see, we have scaled the point size based on the PERSONS attribute. This makes the symbol larger for larger population values like California, New York and Texas and the symbol smaller for smaller population values like Wyoming.
- Press the Save button.
In this session, we took a brief journey to explore SLD styles and various filters in GeoServer. If you want to access the complete tutorial, click on the link.
GeoServer 2.26.2 Release
GeoServer 2.26.2 release is now available with downloads (bin, war, windows), along with docs and extensions.
This is a stable release of GeoServer recommended for production use. GeoServer 2.26.2 is made in conjunction with GeoTools 32.2, GeoWebCache 1.26.2, and ImageIO-Ext 1.4.14.
Thanks to Jody Garnett for making this release.
Security Considerations
This release addresses security vulnerabilities and is recommended.
- CVE-2024-38524 GWC Home Page exposes sensitive server information (Moderate)
- CVE-2025-58360 Unauthenticated XML External Entities (XXE) via WMS GetMap operation (High)
See project security policy for more information on how security vulnerabilities are managed.
File System Sandbox Isolation
A file system sandbox is used to limit access for GeoServer Administrators and Workspace Administrators to specified file folders.
-
A system sandbox is established using
GEOSERVER_FILESYSTEM_SANDBOXapplication property, and applies to the entire application, limiting GeoServer administrators to the<sandbox>folder, and individual workspace administrators into isolated<sandbox>/<workspace>folders. -
A regular sandbox can be configured from the Security > Data screen, and is used to limit individual workspace administrators into
<sandbox>/<workspace>folders to avoid accessing each other’s files.
Thanks to Andrea (GeoSolutions) for this important improvement at the bequest of Munich RE.
Developer Updates
Palantir formatter
A nice update for GeoServer developers is an updated formatter that is both wider at 120 columns, and plays well with the use of lamda expressions.
List<TemplateBuilder> filtered = children.stream()
.filter(b -> b instanceof DynamicValueBuilder || b instanceof SourceBuilder)
.collect(Collectors.toList());
Thanks to Andrea for this improvement, and coordinating the change across all active branches.
Release notes
New Features:
- GEOS-11616 GSIP 229 - File system access isolation
- GEOS-11644 Introducing the rest/security/acl/catalog/reload rest endpoint
Improvement:
- GEOS-11612 Add system property support for Proxy base URL -> use headers activation
- GEOS-11615 Update to Imageio-EXT 1.4.14
- GEOS-11683 MapML WMS Features Coordinate Precision Should be adjusted based on scale
Bug:
- GEOS-11636 Store panels won’t always show feedback in target panels
- GEOS-11494 WFS GetFeature request with a propertyname parameter fails when layer attributes are customized (removed or reordered)
- GEOS-11606 geofence-server imports obsolete asm dep
- GEOS-11611 When Extracting the WFS Service Name from the HTTP Request A Slash Before the Question Marks Causes Issues
- GEOS-11630 REST API throws HTTP 500 When Security Metadata Has Null Attributes
- GEOS-11643 WCS input read limits can be fooled by geotiff reader
- GEOS-11647 Restore “quiet on not found” configuration for REST in global settings
- GEOS-11649 welcome page per-layer is not respecting global service enablement
- GEOS-11672 GWC virtual services available with empty contents
- GEOS-11681 MapML raster GetFeatureInfo not working
Task:
- GEOS-11608 Update Bouncy Castle Crypto package from bcprov-jdk15on:1.69 to bcprov-jdk18on:1.79
- GEOS-11631 Update MySQL driver to 9.1.0
- GEOS-11650 Update dependencies for monitoring-kafka module
- GEOS-11659 Apply Palantir Java format on GeoServer
- GEOS-11671 Upgrade H3 dependency to 3.7.3
- GEOS-11685 Bump jetty.version from 9.4.56.v20240826 to 9.4.57.v20241219
For the complete list see 2.26.2 release notes.
Community Updates
Community module development:
- GEOS-11635 Add support for opaque auth tokens in OpenID connect
- GEOS-11637 DGGS min/max resolution settings stop working after restart
- GEOS-11680 Azure COG assembly lacks mandatory libraries, won’t work
- GEOS-11686 Clickhouse DGGS stores cannot properly read dates
- GEOS-11687 OGC API packages contain gs-web-core
- GEOS-11691 Smart data loader accepts bigint and bigserial but not int8 postgresql type alias
Community modules are shared as source code to encourage collaboration. If a topic being explored is of interest to you, please contact the module developer to offer assistance.
About GeoServer 2.26 Series
Additional information on GeoServer 2.26 series:
GeoServer 3 Crowdfunding Campaign Reaches Major Step: 80% Funding Completion
The GeoServer 3 crowdfunding campaign has made remarkable progress, reaching 80% of its financing goal. A significant boost came from a single €100,000 pledge, underscoring the value of this essential upgrade to the GeoServer platform. With just €112,000 left to raise, now is the time to join the movement and ensure the success of this critical project.

A Campaign with Global Outreach
This initiative, led by a consortium of 3 key companies Camptocamp, GeoCat, and GeoSolutions, has garnered backing from a wide range of contributors, including public institutions, large companies, SMEs and individuals from various countries. The campaign’s extensive outreach demonstrates GeoServer’s importance to a broad spectrum of users worldwide. GeoServer has become a cornerstone in geospatial applications across industries and borders, and this campaign reflects its far-reaching impact.
Why GeoServer 3 Matters
The necessity of implementing GeoServer 3 has never been greater. This major upgrade will deliver:
- Future-proof performance to handle growing data and processing demands.
- Enhanced image processing for better visualization and analysis.
- Improved security to safeguard critical geospatial systems.
- A modernized user experience for easier access and usability.
Without these enhancements, users and providers risk facing limitations in scalability, performance, functionality, and security. Achieving this upgrade will ensure GeoServer remains a leading tool in the geospatial industry, empowering your open-source Spatial Data Infrastructure (SDI) based on GeoServer to innovate continuously while providing secure, high-performance services. This will position your organization at the forefront of geospatial technology.
A Few More Months to Make a Difference
The campaign will continue until spring, providing a limited window for additional financial contributions. While the international team of core contributors is ready to start the migration, we are waiting for the complete budget allocation to begin, in line with the rules of this crowdfunding campaign. To accommodate many entities currently finalizing their budgets, we have planned to let the campaign run for a few more months. This is an excellent opportunity for your organization to support the future of GeoServer and demonstrate your commitment to open-source geospatial solutions.
Every Contribution Counts
With €112,000 still needed to meet the target, every pledge—big or small—matters. Whether you’re a public institution, a large company or an SME, your support can make a difference. Reaching this goal would be a remarkable achievement, building on the strong progress made so far and ensuring the future of GeoServer 3 becomes a reality.
For any questions or to discuss how you can contribute, please email us or fill out the form to pledge your support. Together, we can achieve this milestone and continue building a sustainable, innovative future for geospatial technology.
Thanks to all organizations and individuals that have mobilized themselves, contributed financially, or spread the word to make this campaign a success.
GeoServer 3 is supported by the following organisations:
Individual donations: Abhijit Gujar, Hennessy Becerra, Ivana Ivanova, John Bryant, Jason Horning, Jose Macchi, Peter Smythe, Sajjadul Islam, Sebastiano Meier, Stefan Overkamp.
GeoServer 2025 Roadmap
Happy new year and welcome to 2025 from the GeoServer team!
Last year we started something different for our project - sharing our 2024 roadmap plans with our community and asking for resources (participation and funding) to accomplish some challenging goals. We would like to provide an update for 2025 and a few words on our experience in 2024.

The GeoServer project is supported and maintained thanks to the hard work of volunteers and the backing of public institutions and companies providing professional support.
GeoServer was started in 2001 by a non-profit technology incubator. Subsequent years has seen the project supported by larger companies with investors and venture capital. This support is no longer available - and without this cushion we must rely on our community to play a greater role in the success of the project.
We are seeking a healthy balance in 2025 and are asking for support in the following areas:
-
Maintenance: The GeoServer team uses extensive automation, quality assurance tools, and policy of dropping modules to “right size” the project to match developer resources.
However maintenance costs for software markedly increased in 2024 as did time devoted to security vulnerabilities. This causes the components used by GeoServer to be updated more frequently, and with greater urgency.
✳️ Community members can answer questions on geoserver-user forum, reproduce issues as they are reported, and verify fixes.
✳️ Developers are encouraged to get started by reviewing pull-requests to learn what is needed, and then move on to fixing issues.
-
Security Vulnerabilities: GeoServer works with an established a coordinated vulnerability disclosure policy, with clear guidelines for individuals to particpate based on trust, similar to how committers are managed. Our 2024 experience with CVE-2024-36401 highlights the importance of this activity for our community and service providers.
✳️ Trusted volunteers can help mind geoserver-security email list, and help reproduce vulnerabilities as they are reported. We also seek developer capacity and funding to address confirmed vulnerabilities.
-
Releases: Regular release and community testing is a key success factor for open source projects and is an important priority for GeoServer. Peter has done a great job updating the release instructions, and many of the tasks are automated, making this activity far easier for new volunteers.
✳️ Developers and Service Providers are asked to make time available to to assist with the release process.
Asking our community to test release candidates ahead of each major release has been discontinued due to lack of response. The GeoServer team operates with a time-boxed release model so it is predictable when testing will be expected.
✳️ Community members and Service Providers are asked to help test nightly builds ahead of major releases in March and April.
-
Testing: Testing of new functionality and technology updates is an important quality assurance activity We have had some success asking downstream projects directly to test when facing technical-challenges in 2023.
✳️ We anticipate extensive testing will be required for GeoServer 3 and ask everyone to plan some time to test out nightly builds with your own data and infrastructure during the course of this activity.
-
Sponsorship: In 2023 we made a deliberate effort to “get over being shy” and ask for financial support, setting up a sponsorship page, and listing sponsors on our home page.
The response has not been in keeping with the operational costs of our project and we seek ideas on input on an appropriate approach.
✳️ We ask for your financial assistance in 2025 (see bottom of page for recommendations).
The above priorities of maintenance, testing and sponsorship represent the normal operations of an open-source project. This post is provided as a reminder, and a call to action for our community.
2025 Roadmap Planning
CITE Certification
Our CITE Certification was lost some years ago, due to vandalism of a build server, and we would like to see certification restored.
OGC CITE Certification is important for two reasons:
- Provides a source of black-box testing ensuring that each GeoServer release behaves as intended.
- Provides a logo and visibility for the project helping to promote the use of open standards.
Recent progress on this activity:
- As part of a Camptocamp organized OGCAPI - Features sprint Gabriel was able setup a GitHub workflow restoring the use of CITE testing for black-box testing of GeoServer. Gabriel focused on OGC API - Features certification but found WMS 1.1 and WCS 1.1 tests would also pass out of the box, providing a setup for running the tests in each new pull request.
- Andrea made further progress certifying the output produced by GeoServer, restoring the WMS 1.3, WFS 1.0 and WFS 1.1 tests, as well as upgrading the test engine to the latest production release. In addition, CITE tests that weren’t run in the past have been added, like WFS 2.0 and GeoTIFF, while other new tests are in progress, like WCS 2.0, WMTS 1.0 and GeoPackage.
- The Open Source Geospatial Foundation provides hosting for OSGeo Projects. Peter is looking into this opportunity which would allow the project to be certified and once again be a reference implementation.
✳️ Please reach out on the developer forum and ask how you can help support this activity.
GeoServer 3
GeoServer 3 is being developed to address crucial challenges and ensure that GeoServer remains a reliable and secure platform for the future.
Staying up-to-date with the latest technology is no longer optional — it’s essential. Starting with spring-framework-6, each update requiring several others to occur at the same time.
Our community is responding to this challenge but needs your support to be successful:
-
Brad and David have made considerable progress on Wicket UI updates over the course of 2024, and with Steve’s effort on Content Security Policy compliance (CSP headers are enabled by default in newer versions of Wicket).
-
Andreas Watermeyer (ITS Digital Solutions) has been steadily working on Spring Security 5.8 update and corresponding OAuth2 Secuirty Module replacements.
-
Consortium of Camptocamp, GeoSolutions and GeoCat have responded to our roadmap challenge with a bold GeoServer 3 Crowdfunding. The crowd funding is presently in phase one collecting pledges, when goal is reached phase two will collect funds and start development.
Check out the crowdfunding page for details, faq, including overview of project plan.
✳️ Pledge support for GeoServer 3 Crowdfunding using email or form.
✳️ Developers please reach out on the developer forum if you have capacity to work on this activity.
✳️ Testers GeoServer 3 will need testing with your data and environment over the course of development.
Service Providers
Service providers bring GeoServer technology to a wider audience. We recognize core-contributors who take on an ongoing responsibility for the GeoServer project on our home page, along with a listing of commercial support on our website. We encourage service providers offering GeoServer support to be added to this list.
Helping meet project roadmap planning goals and objectives is a good way for service providers to gain experience with the project and represent their customers in our community. We recognize service providers that contribute to the sustainability of GeoServer as experienced providers.
✳️ We encourage service providers to directly take project maintenance and testing activities, and financially support the project if they do not have capacity to participate directly.
Sponsorship Opportunities
The GeoServer Project Steering Committee uses your financial support to fund maintenance activities, code sprints, and research and development that is beyond the reach of an individual contributor.
GeoServer recognizes your financial support on our home page, sponsorship page and in release notes and presentations. GeoServer is part of the Open Source Geospatial Foundation and your financial support of the project is reflected on the OSGeo sponsorship page.
Recommendations:
- Individuals can use Donate via GitHub Sponsors to have their repository badged as supporting OSGeo.
- Individuals who offer GeoServer services should consider $50 USD a month to be listed as a bronze Sponsor on the OSGeo website.
- Organisations using GeoServer are encouraged to sponsor $50 USD a month to be listed as a bronze sponsor on the OSGeo website.
- Organisations that offer GeoServer services should consider $250 a month to be listed as a silver sponsor on the OSGeo website.
✳️ For instructions on sponsorship see how to Sponsor via Open Source Geospatial Foundation.
Further reading:
Thanks to GeoServer 2025 sponsors:
Using Logical Operators in GeoServer Filters
GeoSpatial Techno is a startup focused on geospatial information that is providing e-learning courses to enhance the knowledge of geospatial information users, students, and other startups. The main approach of this startup is providing quality, valid specialized training in the field of geospatial information.
( YouTube | LinkedIn | Facebook | X )
Using Logical Operators in GeoServer Filters
In this session, we want to talk about the Using logical operators to combine multiple filters in GeoServer. If you want to access the complete tutorial, click on the link.
Introduction
Logical operators in Web Feature Service (WFS) filtering are essential for combining multiple conditions within GeoServer. These operators enable users to construct complex queries, facilitating data retrieval from the WFS service. The primary logical operators include AND, OR, and NOT.
Note. This video was recorded on GeoServer 2.22.4, which is not the most up-to-date version. We encourage all users to use the stable series, currently 2.28.x. To ensure you have the latest release, please visit this link and avoid using older versions of GeoServer.
AND
This operator combines multiple conditions into a single filter expression. The resulting expression matches only those features that meet all of the specified criteria.
- As an example of using this filter in WFS getFeature request, navigate to the Demos page, then select Demo requests.
- From the Request section, select the WFS_getFeature1.0.xml request.
Use the following block codes to replace line 26:
<ogc:And>
<PropertyIsLessThan>
<PropertyName>LAND_KM</PropertyName>
<Literal>100000</Literal>
</PropertyIsLessThan>
<PropertyIsGreaterThan>
<PropertyName>PERSONS</PropertyName>
<Literal>5000000</Literal>
</PropertyIsGreaterThan>
</ogc:And>
Note. In all examples in this blog post, we utilize the topp:states layer.
In this example, we applied a filter to the layer, where the value of the LAND_KM attribute, is less than 100,000 and the PERSONS is greater than 5 million people.
The results include three states: Massachusetts, New Jersey and Indiana.
To use the CQL filtering to apply the equivalent of this example, first, preview the top:states layer in the Layer Preview section. Then, add the filter CQL_FILTER=LAND_KM<100000 And PERSONS>5000000 to the end of the URL.
The complete URL for the layer is as follows:
http://localhost:8080/geoserver/topp/wms?service=WMS&version=1.1.0&request=GetMap&layers=topp%3Astates&bbox=-124.73142200000001,24.955967,-66.969849,49.371735&width=768&height=330&srs=EPSG%3A4326&styles=&format=application/openlayers&CQL_FILTER=LAND_KM<100000 And PERSONS>5000000
OR
This operator allows you to combine multiple conditions and retrieve features that satisfy any of the specified conditions. In simpler terms, at least one condition must be true for the filter to be considered a match.
Here’s an example of how to use the “OR” operator to filter a WFS layer based on two conditions.
<ogc:Or>
<PropertyIsLessThan>
<PropertyName>LAND_KM</PropertyName>
<Literal>100000</Literal>
</PropertyIsLessThan>
<PropertyIsGreaterThan>
<PropertyName>PERSONS</PropertyName>
<Literal>5000000</Literal>
</PropertyIsGreaterThan>
</ogc:Or>
Press the Submit button.
In this example, we filtered the layer to display features that meet either of these conditions: The value of the LAND_KM attribute is less than 100,000 or the PERSONS attribute represents a population greater than 5 million people. The results include 25 states.
To apply the same example using the CQL filtering and observe the results, use the following code in the URL of the layer as mentioned above:
http://localhost:8080/geoserver/topp/wms?service=WMS&version=1.1.0&request=GetMap&layers=topp%3Astates&bbox=-124.73142200000001,24.955967,-66.969849,49.371735&width=768&height=330&srs=EPSG%3A4326&styles=&format=application/openlayers&CQL_FILTER=LAND_KM<100000 Or PERSONS>5000000
NOT
In GeoServer, the NOT operator, also known as the logical negation operator, is used to invert the meaning of a filter expression. It takes one or more filter expressions and returns features that don’t meet the specified conditions.
Here’s an example of using the “NOT” operator for filtering a WFS layer by two conditions:
<ogc:Not>
<ogc:Or>
<PropertyIsLessThan>
<PropertyName>LAND_KM</PropertyName>
<Literal>100000</Literal>
</PropertyIsLessThan>
<PropertyIsGreaterThan>
<PropertyName>PERSONS</PropertyName>
<Literal>5000000</Literal>
</PropertyIsGreaterThan>
</ogc:Or>
</ogc:Not>
Press the Submit button.
In this example, we filtered the layer to show features that don’t meet any of these conditions. That is, neither the value of the LAND_KM attribute is less than 100,000 nor is the value of the PERSONS parameter more than 5 million people. The results include 24 states.
To see how to use the NOT operator in CQL filtering, use the following code at the end of the URL’s layer:
http://localhost:8080/geoserver/topp/wms?service=WMS&version=1.1.0&request=GetMap&layers=topp%3Astates&bbox=-124.73142200000001,24.955967,-66.969849,49.371735&width=768&height=330&srs=EPSG%3A4326&styles=&format=application/openlayers&CQL_FILTER=NOT(LAND_KM<100000 Or PERSONS>5000000)
Combine operators
GeoServer provides the capability of combining logical operators with geometric filters, enhancing the flexibility of WFS filtering. This feature enables users to create more specific and reliable filtering criteria.
Here is an example that effectively uses both spatial and comparison filtering:
<ogc:Filter>
<ogc:And>
<ogc:Intersects>
<ogc:PropertyName>the_geom</ogc:PropertyName>
<gml:LineString xmlns:gml="http://www.opengis.net/gml" srsName="EPSG:4326">
<gml:coordinates>-73.9,43.5 -81.1,38.6 -78.57,35.5</gml:coordinates>
</gml:LineString>
</ogc:Intersects>
<PropertyIsGreaterThanOrEqualTo>
<PropertyName>PERSONS</PropertyName>
<Literal>10000000</Literal>
</PropertyIsGreaterThanOrEqualTo>
</ogc:And>
</ogc:Filter>
In this example, we filtered out states with populations exceeding 10 million, as well as states intersected by a LineString with given coordinates.
Thus, we identified New York and Pennsylvania as the two states that satisfy these conditions.
To see how to use CQL filtering for this example, follow the instance shown on the screen:
CQL_FILTER=INTERSECTS(the_geom,LINESTRING(-73.9 43.5,-81.1 38.6,-78.57 35.5)) AND PERSONS>10000000
As a final example, we examine a comprehensive scenario that incorporates different operators. This example includes a spatial operator, such as the Within filter. Additionally, it showcases two comparison operators, namely PropertyIsLike and PropertyIsGreaterThan.
To better understand these concepts, use the following example:
<ogc:Filter>
<ogc:And>
<ogc:Within>
<ogc:PropertyName>the_geom</ogc:PropertyName>
<gml:Polygon xmlns:gml="http://www.opengis.net/gml" srsName="EPSG:4326">
<gml:outerBoundaryIs>
<gml:LinearRing>
<gml:coordinates>-100,30 -100,45 -80,45 -80,30 -100,30</gml:coordinates>
</gml:LinearRing>
</gml:outerBoundaryIs>
</gml:Polygon>
</ogc:Within>
<ogc:Or>
<ogc:Filter>
<ogc:PropertyIsLike wildCard="%" singleChar="_" escape="!">
<ogc:PropertyName>STATE_NAME</ogc:PropertyName>
<ogc:Literal>%na%</ogc:Literal>
</ogc:PropertyIsLike>
</ogc:Filter>
<PropertyIsGreaterThan>
<PropertyName>STATE_FIPS</PropertyName>
<Literal>30</Literal>
</PropertyIsGreaterThan>
</ogc:Or>
</ogc:And>
</ogc:Filter>
In this example, we use WFS filtering to extract the States that are completely enclosed within specific coordinates. Moreover, we retrieve States whose STATENAME includes the letters “na” or whose STATEFIPS value is greater than 30.
Therefore, we have identified three states that meet the specified criteria: Tennessee, Indiana, and Ohio.
To use the CQL filtering for this example, use the following code:
CQL_FILTER=Within(the_geom,Polygon((-100 30,-100 45,-80 45,-80 30,-100 30))) AND (STATE_NAME LIKE '%na%' OR STATE_FIPS > 30)
In this session, we took a brief journey through the Combining multiple operators for WFS filtering in GeoServer. If you want to access the complete tutorial, click on the link.
Behind The Scenes
- GeoServer 3 First public release date
- GeoServer 3 Sprint Update
- GeoServer 2025 Q4 Developer Update
- GeoServer 3 Crowdfunding Goal Surpassed!
- GeoServer 2025 Q2 Developer Update
- GeoServer 3 Crowdfunding – Last Call!
- GeoServer 3 Crowdfunding Campaign Reaches Major Step: 80% Funding Completion
- GeoServer 2025 Roadmap
- GeoServer 2024 Q4 Developer Update
- GeoServer 3 Call for Crowdfunding