GeoServer Blog
GeoServer 2.23.3 Release
GeoServer 2.23.3 release is now available with downloads (bin, war, windows), along with docs and extensions.
This is a maintenance release of GeoServer providing existing installations with minor updates and bug fixes. GeoServer 2.23.3 is made in conjunction with GeoTools 29.3, and GeoWebCache 1.23.2.
Thanks to Peter Smythe (AfriGIS) for making this release.
Security Considerations
This release addresses security vulnerabilities and is considered an essential upgrade for production systems.
- CVE-2024-23818 Stored Cross-Site Scripting (XSS) vulnerability in WMS OpenLayers Format (Moderate).
- CVE-2024-23640 Stored Cross-Site Scripting (XSS) vulnerability in Style Publisher (Moderate).
- CVE-2023-51445 Stored Cross-Site Scripting (XSS) vulnerability in REST Resources API (Moderate).
This release includes security patches from projects that GeoServer depends on.
- GEOS-11030 Update jetty-server to 9.4.51.v20230217
See project security policy for more information on how security vulnerabilities are managed.
Also, another reminder of the URL check security setting that was introduced in version 2.22.4 and version 2.23.2 (but turned off by default). The latest GeoServer 2.24.0 release has this setting enabled by default. If you are not yet in a position to upgrade to 2.24.0 you are encouraged to enable this recommended setting.
Release notes
New Feature:
- GEOS-11000 WPS process to provide elevation profile for a linestring
Improvement:
- GEOS-10856 geoserver monitor plugin - scaling troubles
- GEOS-11081 Add option to disable GetFeatureInfo transforming raster layers
- GEOS-11087 Fix IsolatedCatalogFacade unnecessary performance overhead
- GEOS-11089 Performance penalty adding namespaces while loading catalog
- GEOS-11090 Use Catalog streaming API in WorkspacePage
- GEOS-11099 ElasticSearch DataStore Documentation Update for RESPONSE_BUFFER_LIMIT
- GEOS-11100 Add opacity parameter to the layer definitions in WPS-Download download maps
- GEOS-11102 Allow configuration of the CSV date format
- GEOS-11114 Improve extensibility in Pre-Authentication scenarios
- GEOS-11116 GetMap/GetFeatureInfo with groups and view params can with mismatched layers/params
- GEOS-11120 Create aggregates filterFunction in OSEO to support STAC Datacube extension implementation
- GEOS-11130 Sort parent role dropdown in Add a new role
- GEOS-11142 Add mime type mapping for yaml files
- GEOS-11148 Update response headers for the Resources REST API
- GEOS-11149 Update response headers for the Style Publisher
- GEOS-11153 Improve handling special characters in the WMS OpenLayers Format
- GEOS-11155 Add the X-Content-Type-Options header
Bug:
- GEOS-10452 Use of Active Directory authorisation seems broken since 2.15.2 (LDAP still works)
- GEOS-11032 Unlucky init order with GeoWebCacheExtension gwcFacade before DiskQuotaMonitor
- GEOS-11138 Jetty unable to start cvc-elt.1.a / org.xml.sax.SAXParseException
- GEOS-11140 WPS download can leak image references in the RasterCleaner
- GEOS-11145 The GUI “wait spinner” is not visible any longer
- GEOS-11166 OGC API Maps HTML representation fail without datetime parameter
Task:
- GEOS-10248 WPSInitializer NPE failure during GeoServer reload
- GEOS-11030 Update jetty-server to 9.4.51.v20230217
- GEOS-11084 Update text field css styling to look visually distinct
- GEOS-11091 Upgrade spring-security to 5.7.10
- GEOS-11092 acme-ldap.jar is compiled with Java 8
- GEOS-11094 Bump org.hsqldb:hsqldb:2.7.1 to 2.7.2
- GEOS-11124 Update json dependency to 20230227 in geowebcache-rest
- GEOS-11141 production consideration for logging configuration hardening
For the complete list see 2.23.3 release notes.
About GeoServer 2.23 Series
Additional information on GeoServer 2.23 series:
- GeoServer 2.23 User Manual
- Drop Java 8
- GUI CSS Cleanup
- Add the possibility to use fixed values in Capabilities for Dimension metadata
- State of GeoServer 2.23
- GeoServer Feature Frenzy 2023
- GeoServer used in fun and interesting ways
- GeoServer Orientation
Release notes: ( 2.23.3 | 2.23.2 | 2.23.1 | 2.23.0 | 2.23-RC1 )
Introducing GeoSpatial Techno with a Video Tutorial
This is a community blog post introducing Geospatial Techno, along with a sample of one of their GeoServer training videos.
GeoSpatial Techno is a startup focused on geospatial information that is providing e-learning courses to enhance the knowledge of geospatial information users, students, and other startups. The main approach of this startup is providing quality, valid specialized training in the field of geospatial information.
( YouTube | LinkedIn | Reddit | Facebook | X )
Getting to know OGC web services and GeoServer software
The course guides you in using GeoServer software to create geospatial web services, styles and publish them step by step simply and practically. Now, before delving into OGC web services, it is important to familiarize yourself with the various types of services.
In this session, we introduced you to the basics of the OGC web services and GeoServer software. If you want to access the complete tutorial, simply click on the link.
I would highly appreciate it if you could subscribe to my channel and share it with your friends to help spread this tutorial. By subscribing, you will gain complete access to the training video, which will enable you to enhance your skills. Moreover, sharing it with your friends guarantees that they can also benefit from this valuable resource. Thank you for your support.
What is Service?
A collection of operations, accessible through an interface, that allows a user to invoke a behavior of value to the user.
What are Web Services?
Web services are internet-based applications that can perform a wide range of functions, from simple tasks to complex business processes.
What are GeoSpatial Web Services?
GeoSpatial web services are online platforms that offer access to and analyze geographical information. They aim to overcome the lack of compatibility between different geospatial systems.
Why do you need standard web services?
Standard web services provide a common platform for communication between modern-day business applications that use different programming languages. This enables convenient interaction regardless of development language.
What is OGC?
The Open Geospatial Consortium (OGC) is an international organization that promotes the use of open standards to make geospatial information and services to be “FAIR”, which stands for Findable, Accessible, Interoperable, and Reusable. This goal applies to various areas such as data sharing, data processing, sensor web, and the Internet of Things.
What are OGC Web Services?
OGC Web Services (OWS) are a set of standards that allow for seamless integration of various online geoprocessing and location services. With OWS, users can access and utilize services such as the Web Map Service (WMS), Web Feature Service (WFS), Web Coverage Service (WCS), and Web Map Tile Service (WMTS).
WMS enables users to retrieve and obtain detailed information on maps of geospatial data. WFS allows for data manipulation operations on geographic features, including querying, creating, modifying, and deleting features. WCS provides access to raster datasets like elevation models and remote sensing imagery. WMTS serves pre-rendered or computed map tiles over the internet.
These services provide an interoperable framework for accessing, integrating, analyzing, and visualizing online geodata sources, sensor-derived information, and geoprocessing capabilities.
What is GeoServer?
GeoServer is a Java-based server that allows users to view and edit geospatial data. Using open standards set forth by the Open Geospatial Consortium (OGC), GeoServer allows for great flexibility in map creation and data sharing.
Open and Share Your Spatial Data
GeoServer is a powerful open-source tool for displaying spatial information through maps in various formats. The tool integrates OpenLayers, a free mapping library, for easy and quick map generation. Moreover, It supports standards like WMS, WFS, WCS, and WMTS, enabling data sharing, editing, and easy integration with web and mobile applications. With modular functionality and extensions, GeoServer offers extensive processing options. For example, the Web Processing Service (WPS) extension provides a wide range of processing options, and users can even create their extensions.
Use Free and Open Source Software
GeoServer is a free and open-source software that brings down the financial barrier to using GIS products. It is released every six months with new features, bug fixes, and improvements, providing a quick turnaround time. This transparent process often leads to faster advancements compared to closed software solutions. By using GeoServer, organizations can avoid software lock-in and save money on support contracts in the future.
Integrate With Mapping APIs
GeoServer is a versatile software that can integrate with popular mapping applications like Google Maps and Microsoft Bing Maps. It can also connect with traditional GIS architectures such as ESRI ArcGIS. OpenLayers and Leaflet are recommended as complementary tools to GeoServer for web mapping needs.
Join the Community
GeoServer has an active global community of users and developers, offering support through email lists. The software has a fixed release cycle and public issue tracker, ensuring transparency and regular updates. Commercial support is also available. Overall, using GeoServer means being part of a supportive community.
GeoServer 2.24.0 Release
GeoServer 2.24.0 release is now available with downloads (bin, war, windows), along with docs and extensions.
This is a stable release of GeoServer recommended for production use. GeoServer 2.24.0 is made in conjunction with GeoTools 30.0, mapfish-print-v2 2.3.0 and GeoWebCache 1.24.0.
Thanks to Peter Smythe (AfriGIS) and Jody Garnett (GeoCat) for making this release.
Thanks to everyone who helped test the release candidate: JP Motaung & Nicolas Kemp, Georg Weickelt, Peter Smythe, Tobia Di Pisa, and Giovanni Allegri.
We would like to thank our 2023 sponsors North River Geographic Systems Inc and How 2 Map for their financial assistance.
Keeping GeoServer sustainable requires a long term community commitment. If you were unable to contribute time testing the release candidate, sponsorship options are available via OSGeo.
Upgrade Notes
GeoServer strives to maintain backwards compatibility allowing for a smooth upgrade experience.
We have one minor change to share in this release:
-
URL Checks: The url check security setting is now enabled by default.
In GeoServer 2.22.5 and 2.23.2 this setting was available for use, but was turned off by default. If you are not yet in a position to upgrade to 2.24.0 you may wish to enable the recommended setting.
Security Considerations
This release addresses security vulnerabilities and is considered an essential upgrade for production systems.
- CVE-2023-43795 WPS Server Side Request Forgery
- CVE-2023-41339 Unsecured WMS dynamic styling sld=url parameter affords blind unauthenticated SSRF
- CVE-2023-51445 Stored Cross-Site Scripting (XSS) vulnerability in REST Resources API (Moderate).
See project security policy for more information on how security vulnerabilities are managed.
IAU authority support and EPSG assumption removal
The new gs-iau extension module provides support for planetary CRSs, sourced from the International Astronomical Union. This allows users to manage GIS data over the Moon, Mars, or even the Sun, with well known, officially supported codes.
In addition to that, many bug fixes occurred in the management of CRSs and their text representations (plain codes, URL, URIs) so that the EPSG authority is no longer assumed to be the only possibility, in a variety of places, such as, for example, GML output. The code base has seen this assumption for twenty long years already, and while we made a good effort to eliminate the assumption, it could be still lurking in some places. Please test and let us know.
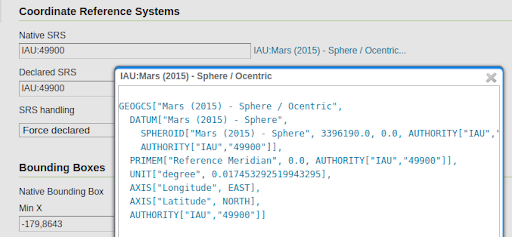
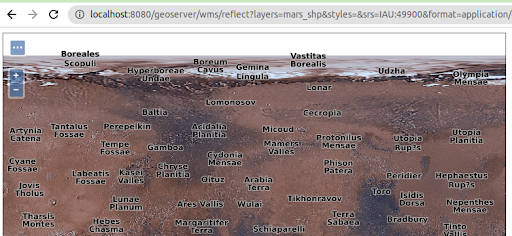
To learn more about this extension please visit the user-guide documentation. Thanks to Andrea Aime (GeoSolutions) for working on this activity.
- GSIP-219 - Multiple CRS authority support, planetary CRS
- GEOS-11075 IAU authority : planetary CRS support
- GEOS-11001 Support other CRS authorities in WFS
- GEOS-11002 Support other CRS authorities in WMS
- GEOS-11056 Support other CRS authorities in WCS
- GEOS-11064 Support other CRS authorities in WPS
- GEOS-11066 Support other CRS authorities in importer
- GEOS-11076 SRSList should show authorities other than EPSG, if available
- GEOS-10970 CatalogBuilder cannot handle CRS in authorities other than EPSG
- GEOS-10971 XStreamPersister cannot save CRS references using authorities other than EPSG
- GEOS-10972 Resource page CRS editors would not work with authorities other than EPSG
GeoServer Printing Extension Updates
The printing extension has seen big changes - with a host of new functionality developed by GeoSolutions over the years. With this update the printing module can now be used out-of-the-box by GeoNode and MapStore (no more customization required).
This update covers the release of MapFish Print 2.3.0 (and restores website user-guide).
GeoServer documentation has been updated with configuration options covering the new functionality.
- Max number of columns configuration for multi column legends
- Simple colored box icon in legends
- Explicit support of GeoServer CQL_FILTER parameter (also with layers merge support): wiki
- Legend fitting
- Don’t break legend items
- Reorder legends block in columns
- Images content
- Dynamic images page
- Multipage legends
- Custom intervals in ScalebarBlock
- Clustering Support wiki
- HTML rendering in text blocks
- Extra Pages
- Group Rendering in attribute blocks
- Skip rendering of pages
- Automatic X-Forwarded-For
- Parsing of Base64 encoded images
Thanks to GeoSolutions for adding functionality to mapfish-print for the GeoNode project. Shout out to Tobia Di Pisa and Giovanni Allegra for integration testing. Jody Garnett (GeoCat) was responsible for updating the mapfish print-lib for Java 11 and gathering up the functionality from different branches and forks. And integrating the updated configuration instructions with the GeoServer User Guide.
- GEOS-11159 Update mapfish-print-lib 2.3.0
New Security > URL Checks page
The previous 2.23 series added a new Check URL facility under the Security menu, but it was turned off by default, for backwards compatibility reasons. This functionality allows administrators to manage OGC Service use of external resources.
This has been included in GeoServer 2.22.x and 2.23.x series for backwards compatibility.
Backwards compatibility note:: This functionality is turned ON by default from GeoServer 2.24.0 onwards.
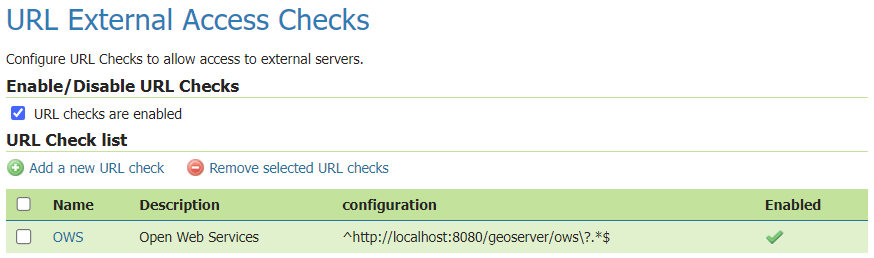
For information and examples on how to use the URL Check page, visit user guide documentation.
- GSIP 218 - Control remote HTTP requests sent by GeoTools \ GeoServer
- GEOS-10949 Control remote resources accessed by GeoServer
- GEOS-11048 Improve URL checking
Project Updates
Updated Security Policy
This release follows a revised security policy. Our existing “responsible disclosure policy” has been renamed, the practice is now called “coordinated vulnerability disclosure.” Last year we enabled GitHub private vulnerability reporting, we will now use these facilities to issue CVE numbers.
Coordinated vulnerability disclosure
Disclosure policy:
- The reported vulnerability has been verified by working with the geoserver-security list
- GitHub security advisory is used to reserve a CVE number
- A fix or documentation clarification is accepted and backported to both the “stable” and “maintenance” branches
- A fix is included for the “stable” and “maintenance” downloads (released as scheduled, or issued via emergency update)
- The CVE vulnerability is published with mitigation and patch instructions
This represents a balance between transparency and participation that does not overwhelm participants. Those seeking greater visibility are encouraged to volunteer with the geoserver-security list; or work with one of the commercial support providers who participate on behalf of their customers.
This change has already resulted in improved interaction with security researchers.
Thanks to Jody Garnett (GeoCat) for this proposal on behalf of GeoCat Live customers.
Developer updates
Internal refactor to remove “org.opengis” package usage
The GeoTools project moved away from using the org.opengis package after complaints from OGC GeoAPI working group representatives, using
the same package name. Interfaces have been moved to the org.geotool.api package, along with some general clean up.
While this does not affect GeoServer users directly, it’s of consequence for those that have installations with custom, home grown plugins that might have to be migrated as a consequence. For those, the GeoTools project offers a migration guide, along with a refactoring script that might perform the migration for you, or else, get you close to a working point. GeoServer itself has been migrated using these scripts, with minimal manual intervention.
For more details, and access to the migration script, please see the GeoTools 30 upgrade guide.
Thanks to Jody Garnett (GeoCat), Andrea Aime (GeoSolutions), and Ian Turton (ASTUN Technologies) for all the hard work on this activity. We would also like to thank the Open Source Geospatial Foundation for setting up a cross-project activity and financial support to address this requested change.
- GEOS-11070 Upgrading to GeoTools 30.x series, refactor to
org.geotools.apiinterfaces
Community modules updates
While not strictly part of this release, it’s interesting to know about some community module advances that can be found only in the the 2.24.x series.
Two extensions are no longer actively supported and are now available as community modules:
- GEOS-10960 Downgrade imagemap module to community
- GEOS-10961 Downgrade xslt extension to community
The following community modules have been removed (due to lack of interest):
- GEOS-10962 Remove wms-eo community module
- GEOS-10963 Remove SAML community module
- GEOS-10966 Remove importer-fgdb community module
- GEOS-10967 Remove teradata community module
- GEOS-10977 Remove wmts-styles community module
- GEOS-10978 Remove nsg-wmts community module
- GEOS-10984 Remove ows-simulate community module
OGC API community modules continues to improve
The OGC API community module keeps improving. In particular, thanks to the GeoNovum sponsorship, GeoSolutions made the OGC API Features module pass the OGC CITE compliance tests, for the “core” and “CRS by reference” conformance classes. Along with this work, other significant changes occurred:
- Made the API version number appear in the service path, easing future upgrades
- Support for configurable links, required to get INSPIRE download service compliance.
In addition to that, the new “search” experimental conformance class allows to POST complex searches against collections, as a JSON document, in a way similar to the STAC API.
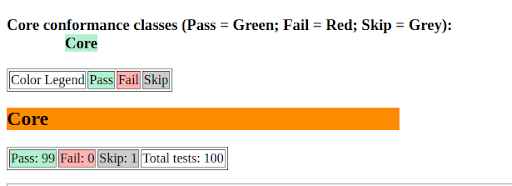
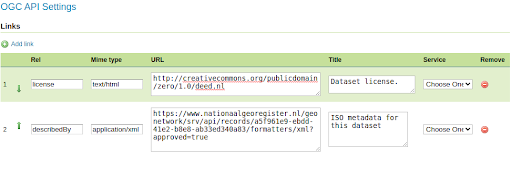
Those interested in this work are encouraged to contact Andrea Aime (GeoSolutions).
- GEOS-10924 Support JSON-FG draft encoding in OGC API - Features
- GEOS-11045 Implement proposal “OGC API - Features - Part n: Query by IDs”
- GEOS-10882 Add an option to remove trailing slash match in OGC APIs
- GEOS-10887 Add angle brackets to OGC API CRS Header
- GEOS-10892 Allow configuring custom links for OGC API “collections” and single collection resources
- GEOS-10895 Make OGC API CITE compliant even if the trailing slash is disabled: landing page exception
- GEOS-11058 Support other CRS authorities in OGC APIs
- GEOS-10909 Don’t link from OGC API Features to WFS 2.0 DescribeFeatureType output, if WFS is disabled
- GEOS-10954 Split ogcapi community module package into single functionality packages
DataDir Catalogue loader
For folks working with very large catalogues some improvement from cloud native geoserver are now available to reduce startup time.
Thanks to Gabriel Roldan for folding this improvement into a community module for the rest of the GeoServer community to enjoy.
- GEOS-11049 Community module “datadir catalog loader”
GeoServer Access Control List Project
The GeoServer Access Control List project is an independent application service that manages access rules, and a GeoServer plugin that requests authorization limits on a per-request basis.
Gabriel Roldan is the contact point for anyone interested in this work.
The vector mosaic and FlatGeoBuf modules sport significant performance improvements
FlatGeoBuf is a “performant binary encoding for geographic data”, a single file format that also manages to be cloud native and include a spatial index. GeoServer provides access to this format thought the WFS FlatGeobuf output format, which not only can write the format, but also read it as a standard data store.
The Vector Mosaic datastore supports creation of mosaics made of single file vector data, useful in situations where the access to data is targeted to sub-pages of a larger data set (e.g., data for a single time, or a single customer, or a single data collect, out of a very large uniform set of vectors) and the database storage for it has become either too slow, or too expensive.
These two modules make a great combo for those in need to handle very large vector datasets, by storing the FlatGeoBuf on cheap storage.
In particular, the FlatGeoBuf module saw speed improvements that made it the new “fastest vector format” for cases where one needs to display a large data set, all at once, on screen (PostGIS remains the king of the hill for anything that needs sophisticated filtering instead).
For reference, we have timed rendering 4 million tiny polygons out of a precision farming collect, using a 7 classes quantile based SLDs. Here is a tiny excerpt of the map:

And here are the timings to render the full set of polygons, putting them all on screen, at the same time, with a single GetMap request:
- PostGIS, 113 seconds
- Shapefile, 41 seconds
- Flatgeobuf, 36 seconds
The tuning is not complete, more optimizations are possible. Interested? Andrea Aime is the contact point for this work.
Release notes
(Including the changes made in 2.24-RC, the release candidate)
Improvement:
- GEOS-11114 Improve extensibility in Pre-Authentication scenarios
- GEOS-11130 Sort parent role dropdown in Add a new role
- GEOS-11142 Add mime type mapping for yaml files
- GEOS-11148 Update response headers for the Resources REST API
- GEOS-11149 Update response headers for the Style Publisher
- GEOS-10926 Community Module Proxy-Base-Ext
- GEOS-10934 CSW does not show title/abstract on welcome page
- GEOS-10973 DWITHIN delegation to mongoDB
- GEOS-10999 Make GeoServer KML module rely on HSQLDB instead of H2
- GEOS-11005 Make sure H2 dependencies are included in the packages of optional modules that still need it
- GEOS-11059 Map preview should not assume EPSG authority
- GEOS-11081 Add option to disable GetFeatureInfo transforming raster layers
- GEOS-11087 Fix IsolatedCatalogFacade unnecessary performance overhead
- GEOS-11090 Use Catalog streaming API in WorkspacePage
- GEOS-11099 ElasticSearch DataStore Documentation Update for RESPONSE_BUFFER_LIMIT
- GEOS-11100 Add opacity parameter to the layer definitions in WPS-Download download maps
- GEOS-11102 Allow configuration of the CSV date format
- GEOS-11116 GetMap/GetFeatureInfo with groups and view params can with mismatched layers/params
Bug:
- GEOS-11138 Jetty unable to start cvc-elt.1.a / org.xml.sax.SAXParseException
- GEOS-11140 WPS download can leak image references in the RasterCleaner
- GEOS-11145 The GUI “wait spinner” is not visible any longer
- GEOS-8162 CSV Data store does not support relative store paths
- GEOS-10452 Use of Active Directory authorisation seems broken since 2.15.2 (LDAP still works)
- GEOS-10874 Log4J: Windows binary zip release file with log4j-1.2.14.jar
- GEOS-10875 Disk Quota JDBC password shown in plaintext
- GEOS-10899 Features template escapes twice HTML produced outputs
- GEOS-10903 WMS filtering with Filter 2.0 fails
- GEOS-10921 Double escaping of HTML with enabled features-templating
- GEOS-10922 Features templating exception on text/plain format
- GEOS-10928 Draft JSON-FG Implementation for OGC API - Features
- GEOS-10936 YSLD and OGC API modules are incompatible
- GEOS-10937 JSON-FG reprojected output should respect authority axis order
- GEOS-10958 Update Spotbugs to 4.7.3
- GEOS-10981 Slow CSW GetRecords requests with JDBC Configuration
- GEOS-10985 Backup Restore of GeoServer catalog is broken with GeoServer 2.23.0 and StAXSource
- GEOS-10993 Disabled resources can cause incorrect CSW GetRecords response
- GEOS-11015 geopackage wfs output builds up tmp files over time
- GEOS-11016 Docker nightly builds use outdated GeoServer war
- GEOS-11033 WCS DescribeCoverage ReferencedEnvelope with null crs
- GEOS-11060 charts and mssql extension zips are missing the extension
Task:
- GEOS-11134 Feedback on download bundles: README, RUNNING, GPL html files
- GEOS-11141 production consideration for logging configuration hardening
- GEOS-11091 Upgrade spring-security to 5.7.10
- GEOS-11094 Bump org.hsqldb:hsqldb:2.7.1 to 2.7.2
- GEOS-11103 Upgrade Hazelcast version to 5.3.x
- GEOS-10248 WPSInitializer NPE failure during GeoServer reload
- GEOS-10904 Bump jettison from 1.5.3 to 1.5.4
- GEOS-10907 Update spring.version from 5.3.25 to 5.3.26
- GEOS-10941 Update ErrorProne to 2.18
- GEOS-10987 Bump xalan:xalan and xalan:serializer from 2.7.2 to 2.7.3
- GEOS-10988 Update spring.version from 5.3.26 to 5.3.27 and spring-integration.version from 5.5.17 to 5.5.18
- GEOS-11010 Upgrade guava from 30.1 to 32.0.0
- GEOS-11011 Upgrade postgresql from 42.4.3 to 42.6.0
- GEOS-11012 Upgrade commons-collections4 from 4.2 to 4.4
- GEOS-11018 Upgrade commons-lang3 from 3.8.1 to 3.12.0
- GEOS-11019 Upgrade commons-io from 2.8.0 to 2.12.0
- GEOS-11020 Add test scope to mockito-core dependency
- GEOS-11062 Upgrade httpclient from 4.5.13 to 4.5.14
- GEOS-11063 Upgrade httpcore from 4.4.10 to 4.4.16
- GEOS-11067 Upgrade wiremock to 2.35.0
- GEOS-11080 Remove ASCII grid output format from WCS
- GEOS-11084 Update text field css styling to look visually distinct
- GEOS-11092 acme-ldap.jar is compiled with Java 8
For the complete list see 2.24.0 release notes.
About GeoServer 2.24 Series
Additional information on GeoServer 2.24 series:
GeoServer 2.24-RC Release
GeoServer 2.24-RC release is now available with downloads (bin, war, windows), along with docs and extensions.
This is a release candidate intended for public review and feedback, made in conjunction with GeoTools 30-RC, GeoWebCache 1.24-RC, mapfish-print-v2 2.3-RC and geofence-3.7-RC.
Thanks to Andrea Aime (GeoSolutions) and Jody Garnett (GeoCat) for working on making this release candidate.
Release candidate public testing and feedback
Testing and providing feedback on releases is part of the open-source social contract. The development team (and their employers and customers) are responsible for sharing this great technology with you.
The collaborative part of open-source happens now - we ask you to test this release candidate in your environment and with your data. Try out the new features, double check if the documentation makes sense, and most importantly let us know!
If you spot something that is incorrect or not working do not assume it is obvious and we will notice. We request and depend on your email and bug reports at this time. If you are working with commercial support your provider is expected to participate on your behalf.
Keeping GeoServer sustainable requires a long term community commitment. If you are unable to contribute time, sponsorship options are available via OSGeo.
IAU authority support and EPSG assumption removal
The new gs-iau extension module provides support for planetary CRSs, sourced from the International Astronomical Union. This allows to manage GIS data over the Moon, Mars, or even the Sun, with well known, officially supported codes.
In addition to that, many bug fixes occurred in the management of CRSs and their text representations (plain codes, URL, URIs) so that the EPSG authority is no longer assumed to be the only possibility, in a variety of places, such as, for example, GML output. The code base has seen this assumption for twenty years long, and while we made a good effort to eliminate the assumption, it could be still lurking in some places. Please test and let us know.


To learn more about this extension please visit the user-guide documentation. Thanks to Andrea Aime (GeoSolutions) for working on this activity.
- GSIP-219 - Multiple CRS authority support, planetary CRS
- GEOS-11075 IAU authority : planetary CRS support
- GEOS-11001 Support other CRS authories in WFS
- GEOS-11002 Support other CRS authorities in WMS
- GEOS-11056 Support other CRS authorities in WCS
- GEOS-11064 Support other CRS authorities in WPS
- GEOS-11066 Support other CRS authorities in importer
- GEOS-11076 SRSList should show authorities other than EPSG, if available
- GEOS-10970 CatalogBuilder cannot handle CRS in authorities other than EPSG
- GEOS-10971 XStreamPersister cannot save CRS references using authorities other than EPSG
- GEOS-10972 Resource page CRS editors would not work with authorities other than EPSG
GeoServer Printing Extension Updates
The printing extension has seen big changes - with a host of new functionality developed by GeoSolutions over the years. With this update the printing module can now be used out-of-the-box by GeoNode and MapStore (no more customization required).
- Max number of columns configuration for multi column legends
- Simple colored box icon in legends
- Explicit support of Geoserver CQL_FILTER parameter (also with layers merge support)
- Legend fitting
- Don’t break legend items
- Reorder legends block in columns
- Images content
- Dynamic images page
- Multipage legends
- Custom intervals in ScalebarBlock
- Clustering Support
- HTML rendering in text blocks
- Extra Pages
- Group Rendering in attribute blocks
- Skip rendering of pages
- Automatic X-Forwarded-For
- Parsing of Base64 encoded images
Thanks to GeoSolutions for adding functionality to mapfish-print for the GeoNode project. Jody Garnett (GeoCat) was responsible for updating the mapfish print-lib for Java 11 and gathering up the functionality from different branches and forks.
- GEOS-11132 mapfish-print-v2 2.3-RC
New Security > URL Checks page
This release adds a new Check URL facility under the Security menu. This allows administrators to manage OGC Service use of external resources.

For information and examples on how to use the URL Check page, visit user guide documentation.
- GSIP 218 - Control remote HTTP requests sent by GeoTools \ GeoServer
- GEOS-10949 Control remote resources accessed by GeoServer
- GEOS-11048 Improve URL checking
Developer updates
Internal refactor to remove “org.opengis” package usage
The GeoTools project moved away from using the “org.opengis” package after complaints from OGC GeoAPI working group representatives, using the same package name. Interfaces have been moved to the “org.geotool.api” package, along with some general clean up.
While this does not affect GeoServer users directly, it’s of consequence for those that have installation with custom, home grown plugins that might have to be migrated as a consequence. For those, the GeoTools project offers a migration guide, along with a refactoring script that might perform the migration for you, or else, get you close to a working point. GeoServer itself has been migrated using these scripts, with minimal manual intervention.
For more details, and access to the migration script, please see the GeoTools 30 upgrade guide.
Thanks to Jody Garnett (GeoCat), Andrea Aime (GeoSolutions), and Ian Turton (ASTUN Technologies) for all the hard work on this activity. We would also like to thank the Open Source Geospatial Foundation for setting up a cross-project activity and financial support to address this requested change.
- GEOS-11070 Upgrading to GeoTools 30.x series, refactor to org.geotools.api interfaces
Community modules updates
While not strictly part of this release, it’s interesting to know about some community module advances that can be found only in the the 2.24.x series.
Two extensions are no longer actively supported and are now available as community modules:
- GEOS-10960 Downgrade imagemap module to community
- GEOS-10961 Downgrade xslt extension to community
The following community modules have been removed (due to lack of interest):
- GEOS-10962 Remove wms-eo community module
- GEOS-10963 Remove SAML community module
- GEOS-10966 Remove importer-fgdb community module
- GEOS-10967 Remove teradata community module
- GEOS-10977 Remove wmts-styles community module
- GEOS-10978 Remove nsg-wmts community module
- GEOS-10984 Remove ows-simulate community module
OGC API community modules continues to improve
The OGC API community module keeps improving. In particular, thanks to the GeoNovum sponsorship, GeoSolutions made the OGC API Features module pass the OGC CITE compliance tests, for the “core” and “CRS by reference” conformance classes. Along with this work, other significant changes occurred:
- Made the API version number appear in the service path, easing future upgrades
- Support for configurable links, required to get INSPIRE download service compliance.
In addition to that, the new “search” experimental conformance class allows to POST complex searches against collections, as a JSON document, in a way similar to the STAC API.


Those interested in this work are encouraged to contact Andrea Aime (GeoSolutions).
- GEOS-10924 Support JSON-FG draft encoding in OGC API - Features
- GEOS-11045 Implement proposal “OGC API - Features - Part n: Query by IDs”
- GEOS-10882 Add an option to remove trailing slash match in OGC APIs
- GEOS-10887 Add angle brackets to OGC API CRS Header
- GEOS-10892 Allow configuring custom links for OGC API “collections” and single collection resources
- GEOS-10895 Make OGC API CITE compliant even if the trailing slash is disabled: landing page exception
- GEOS-11058 Support other CRS authorities in OGC APIs
- GEOS-10909 Don’t link from OGC API Features to WFS 2.0 DescribeFeatureType output, if WFS is disabled
- GEOS-10954 Split ogcapi community module package into single functionality packages
DataDir Catalogue loader
For folks working with very large catalogues some improvement from cloud native geoserver are now available to reduce startup time.
Thanks to Gabriel Roldan for folding this improvement into a community module for the rest of the GeoServer community to enjoy.
- GEOS-11049 Community module “datadir catalog loader”
GeoServer Access Control List Project
The GeoServer Access Control List project is an independent application service that manages access rules, and a GeoServer plugin that requests authorization limits on a per-request basis.
Gabriel Roldan is the contact point for anyone interested in this work.
The vector mosaic and FlatGeoBuf modules sport significant performance improvements
FlatGeoBuf is a “A performant binary encoding for geographic data”, a single file format that also manages to be cloud native and include a spatial index. GeoServer provides access to this format thought the WFS FlatGeobuf output format, which not only can write the format, but also read it as a standard data store.
The Vector Mosaic datastore supports creation of mosaics made of single file vector data, useful in situations where the access to data is targeted to sub-pages of a larger data set (e.g., data for a single time, or a single customer, or a single data collect, out of a very large uniform set of vectors) and the database storage for it is become either too slow, or too expensive.
These two modules make a great combo for those in need to handle very large vector datasets, by storing the FlatGeoBuf on cheap storage.
In particular, the FlatGeoBuf module saw speed improvements that made it the new “fastest vector format” for cases where one needs to display a large data set, all at once, on screen (PostGIS remains the king of the hill for anything that needs sophisticated filtering instead).
For reference, we have timed rendering 4 million tiny polygons out of a precision farming collect, using a 7 classes quantile based SLDs. Here is a tiny excerpt of the map:

And here are the timings to render the full set of polygons, putting them all on screen, at the same time, with a single GetMap request:
- PostGIS, 113 seconds
- Shapefile, 41 seconds
- Flatgeobuf, 36 seconds
The tuning is not complete, more optimizations are possible. Interested? Andrea Aime is the contact point for this work.
Release notes
New Feature:
- GEOS-10992 Make GWC UI for disk quota expose HSQLDB, remove H2, automatically update existing installations
- GEOS-11000 WPS process to provide elevation profile for a linestring
Improvement:
- GEOS-10926 Community Module Proxy-Base-Ext
- GEOS-10934 CSW does not show title/abstract on welcome page
- GEOS-10973 DWITHIN delegation to mongoDB
- GEOS-10999 Make GeoServer KML module rely on HSQLDB instead of H2
- GEOS-11005 Make sure H2 dependencies are included in the packages of optional modules that still need it
- GEOS-11059 Map preview should not assume EPSG authority
- GEOS-11081 Add option to disable GetFeatureInfo transforming raster layers
- GEOS-11087 Fix IsolatedCatalogFacade unnecessary performance overhead
- GEOS-11090 Use Catalog streaming API in WorkspacePage
- GEOS-11099 ElasticSearch DataStore Documentation Update for RESPONSE_BUFFER_LIMIT
- GEOS-11100 Add opacity parameter to the layer definitions in WPS-Download download maps
- GEOS-11102 Allow configuration of the CSV date format
- GEOS-11116 GetMap/GetFeatureInfo with groups and view params can with mismatched layers/params
Bug:
- GEOS-8162 CSV Data store does not support relative store paths
- GEOS-10452 Use of Active Directory authorisation seems broken since 2.15.2 (LDAP still works)
- GEOS-10874 Log4J: Windows binary zip release file with log4j-1.2.14.jar
- GEOS-10875 Disk Quota JDBC password shown in plaintext
- GEOS-10899 Features template escapes twice HTML produced outputs
- GEOS-10903 WMS filtering with Filter 2.0 fails
- GEOS-10921 Double escaping of HTML with enabled features-templating
- GEOS-10922 Features templating exception on text/plain format
- GEOS-10928 Draft JSON-FG Implementation for OGC API - Features
- GEOS-10936 YSLD and OGC API modules are incompatible
- GEOS-10937 JSON-FG reprojected output should respect authority axis order
- GEOS-10958 Update Spotbugs to 4.7.3
- GEOS-10981 Slow CSW GetRecords requests with JDBC Configuration
- GEOS-10985 Backup Restore of GeoServer catalog is broken with GeoServer 2.23.0 and StAXSource
- GEOS-10993 Disabled resources can cause incorrect CSW GetRecords response
- GEOS-11015 geopackage wfs output builds up tmp files over time
- GEOS-11016 Docker nightly builds use outdated GeoServer war
- GEOS-11033 WCS DescribeCoverage ReferencedEnvelope with null crs
- GEOS-11060 charts and mssql extension zips are missing the extension
Task:
- GEOS-11091 Upgrade spring-security to 5.7.10
- GEOS-11094 Bump org.hsqldb:hsqldb:2.7.1 to 2.7.2
- GEOS-11103 Upgrade Hazelcast version to 5.3.x
- GEOS-10248 WPSInitializer NPE failure during GeoServer reload
- GEOS-10904 Bump jettison from 1.5.3 to 1.5.4
- GEOS-10907 Update spring.version from 5.3.25 to 5.3.26
- GEOS-10941 Update ErrorProne to 2.18
- GEOS-10987 Bump xalan:xalan and xalan:serializer from 2.7.2 to 2.7.3
- GEOS-10988 Update spring.version from 5.3.26 to 5.3.27 and spring-integration.version from 5.5.17 to 5.5.18
- GEOS-11010 Upgrade guava from 30.1 to 32.0.0
- GEOS-11011 Upgrade postgresql from 42.4.3 to 42.6.0
- GEOS-11012 Upgrade commons-collections4 from 4.2 to 4.4
- GEOS-11018 Upgrade commons-lang3 from 3.8.1 to 3.12.0
- GEOS-11019 Upgrade commons-io from 2.8.0 to 2.12.0
- GEOS-11020 Add test scope to mockito-core dependency
- GEOS-11062 Upgrade httpclient from 4.5.13 to 4.5.14
- GEOS-11063 Upgrade httpcore from 4.4.10 to 4.4.16
- GEOS-11067 Upgrade wiremock to 2.35.0
- GEOS-11080 Remove ASCII grid output format from WCS
- GEOS-11084 Update text field css styling to look visually distinct
- GEOS-11092 acme-ldap.jar is compiled with Java 8
For the complete list see 2.24-RC release notes.
About GeoServer 2.24 Series
Additional information on GeoServer 2.24 series:
- Control remote HTTP requests sent by GeoTools/GeoServer
- Multiple CRS authority support, planetary CRS
Release notes: ( 2.24-RC )
GeoServer 2.22.5 Release
GeoServer 2.22.5 release is now available with downloads ( bin, war, windows) , along with docs and extensions.
This is a maintenance release of GeoServer providing existing installations with minor updates and bug fixes. GeoServer 2.22.5 is made in conjunction with GeoTools 28.5.
Thanks to Peter Smythe (AfriGIS) for making this release.
2023-09-05 update: GeoServer 2.22.5 has been recompiled and uploaded to SourceForge. The initial upload was accidentally compiled with Java 11 and would not function in a Java 8 environment.
Thanks to Jody Garnett (GeoCat) for this update, and Steve Ikeoka for testing in a Java 8 environment.
Java 8 End-of-life
This GeoServer 2.22.5 maintenance release is final scheduled release of GeoServer 2.22.x series, and thus the last providing Java 8 support.
All future releases will require a minimum of Java 11.
Security Considerations
This release addresses security vulnerabilities and is considered an essential upgrade for production systems.
- CVE-2023-43795 WPS Server Side Request Forgery
- CVE-2023-41339 Unsecured WMS dynamic styling sld=url parameter affords blind unauthenticated SSRF
See project security policy for more information on how security vulnerabilities are managed.
Release notes
Improvement:
- GEOS-10856 geoserver monitor plugin - scaling troubles
- GEOS-11048 Improve URL checking
- GEOS-11081 Add option to disable GetFeatureInfo transforming raster layers
- GEOS-11099 ElasticSearch DataStore Documentation Update for RESPONSE_BUFFER_LIMIT
- GEOS-11100 Add opacity parameter to the layer definitions in WPS-Download download maps
Bug:
- GEOS-10874 Log4J: Windows binary zip release file with log4j-1.2.14.jar
- GEOS-10875 Disk Quota JDBC password shown in plaintext
- GEOS-10901 GetCapabilities lists the same style multiple times when used as both a default and alternate style
- GEOS-10903 WMS filtering with Filter 2.0 fails
- GEOS-10932 csw-iso: should only add ‘xsi:nil = false’ attribute
- GEOS-11025 projection parameter takes no effect on MongoDB Schemaless features WFS requests
- GEOS-11035 Enabling OSEO from Workspace Edit Page Results in an NPE
- GEOS-11054 NullPointerException creating layer with REST, along with attribute list
- GEOS-11055 Multiple layers against the same ES document type conflict with each other
- GEOS-11069 Layer configuration page doesn’t work for broken SQL views
Task:
- GEOS-11062 Upgrade httpclient from 4.5.13 to 4.5.14
- GEOS-11063 Upgrade httpcore from 4.4.10 to 4.4.16
- GEOS-11067 Upgrade wiremock to 2.35.0
- GEOS-11092 acme-ldap.jar is compiled with Java 8
For the complete list see 2.22.5 release notes.
About GeoServer 2.22 Series
Additional information on GeoServer 2.22 series:
- GeoServer 2.22 User Manual
- Update Instructions
- Metadata extension
- CSW ISO Metadata extension
- State of GeoServer (FOSS4G Presentation)
- GeoServer Beginner Workshop (FOSS4G Workshop)
- Welcome page (User Guide)
Release notes: ( 2.22.5 | 2.22.4 | 2.22.3 | 2.22.2 | 2.22.1 | 2.22.0 | 2.22-RC | 2.22-M0 )
Behind The Scenes
- GeoServer 3 First public release date
- GeoServer 3 Sprint Update
- GeoServer 2025 Q4 Developer Update
- GeoServer 3 Crowdfunding Goal Surpassed!
- GeoServer 2025 Q2 Developer Update
- GeoServer 3 Crowdfunding – Last Call!
- GeoServer 3 Crowdfunding Campaign Reaches Major Step: 80% Funding Completion
- GeoServer 2025 Roadmap
- GeoServer 2024 Q4 Developer Update
- GeoServer 3 Call for Crowdfunding
