GeoServer Blog
GeoServer 2.23.2 Release
GeoServer 2.23.2 release is now available with downloads ( bin, war, windows) , along with docs and extensions.
This is a stable release of GeoServer recommended production use. GeoServer is made in conjunction with GeoTools 29.2, and GeoWebCache 1.23.1.
Thanks to Ian Turton for making this release.
Security Considerations
This release addresses security vulnerabilities and is considered an essential upgrade for production systems.
- CVE-2023-43795 WPS Server Side Request Forgery
- CVE-2023-41339 Unsecured WMS dynamic styling sld=url parameter affords blind unauthenticated SSRF
- CVE-2024-23643 Stored Cross-Site Scripting (XSS) vulnerability in GWC Seed Form (Moderate).
2024-06-30 Update: The following mitigation has been provided:
-
CVE-2024-36401 Remote Code Execution (RCE) vulnerability in evaluating property name expressions (Critical)
geoserver-2.23.2-patches.zip (replacing
gt-app-schema,gt-complexandgt-xsd-corejars) has been provided by Andrea (GeoSolutions)
See project security policy for more information on how security vulnerabilities are managed.
New Security > URL Checks page
This release adds a new Check URL facility under the Security menu. This allows administrators to manage OGC Service use of external resources.
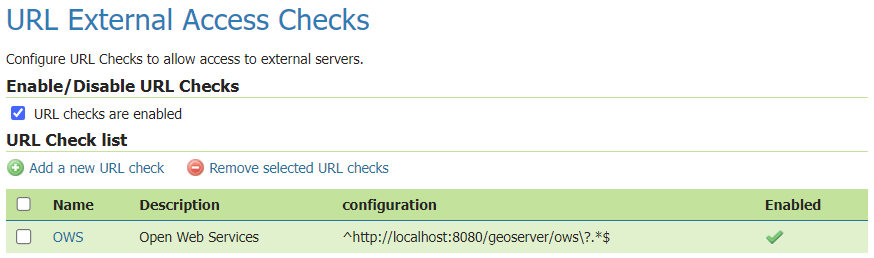
For information and examples on how to use the URL Check page, visit user guide documentation.
- GEOS-10949 URL checks for remote resources accessed by GeoServer
- GSIP 218 - Control remote HTTP requests sent by GeoTools \ GeoServer
Release notes
New Feature:
- GEOS-10949 Control remote resources accessed by GeoServer
- GEOS-10992 Make GWC UI for disk quota expose HSQLDB, remove H2, automatically update existing installations
Improvement:
- GEOS-10973 DWITHIN delegation to mongoDB
- GEOS-11048 Improve URL checking
Bug:
- GEOS-10874 Log4J: Windows binary zip release file with log4j-1.2.14.jar
- GEOS-10875 Disk Quota JDBC password shown in plaintext
- GEOS-10901 GetCapabilities lists the same style multiple times when used as both a default and alternate style
- GEOS-10903 WMS filtering with Filter 2.0 fails
- GEOS-10906 Authentication not sent if connection pooling activated
- GEOS-10932 csw-iso: should only add ‘xsi:nil = false’ attribute
- GEOS-10936 YSLD and OGC API modules are incompatible
- GEOS-10964 Support virtual services for OSEO/STAC
- GEOS-10980 CSS extension lacks ASM JARs as of 2.23.0, stops rendering layer when style references a file
- GEOS-10981 Slow CSW GetRecords requests with JDBC Configuration
- GEOS-10982 Wicket bug when trying to add new Vector Attribute (build 2.23 on Tomcat/Windows)
- GEOS-10993 Disabled resources can cause incorrect CSW GetRecords response
- GEOS-10994 OOM due to too many dimensions when range requested
- GEOS-10997 GetCapabilities broken when using Data Security Layer groups
- GEOS-10998 LayerGroupContainmentCache is being rebuilt on each ApplicationEvent
- GEOS-11015 geopackage wfs output builds up tmp files over time
- GEOS-11024 metadata: add datetime field type to feature catalog
- GEOS-11025 projection parameter takes no effect on MongoDB Schemaless features WFS requests
- GEOS-11026 ClassNotFoundException: org.h2.driver on shutdown
- GEOS-11033 WCS DescribeCoverage ReferencedEnvelope with null crs
- GEOS-11035 Enabling OSEO from Workspace Edit Page Results in an NPE
- GEOS-11036 The OAuth2/OIDC security filters do not work as expected anymore after the spring-security-core depencency update to 5.7.8
- GEOS-11046 Styles using the custom mark
shape://dotdon’t draw any fill - GEOS-11054 NullPointerException creating layer with REST, along with attribute list
- GEOS-11055 Multiple layers against the same ES document type conflict with each other
- GEOS-11060 charts and mssql extension zips are missing the extension
- GEOS-11069 Layer configuration page doesn’t work for broken SQL views
Task:
- GEOS-10987 Bump xalan:xalan and xalan:serializer from 2.7.2 to 2.7.3
- GEOS-10988 Update spring.version from 5.3.26 to 5.3.27 and spring-integration.version from 5.5.17 to 5.5.18
- GEOS-11008 Update sqlite-jdbc from 3.34.0 to 3.41.2.2
- GEOS-11010 Upgrade guava from 30.1 to 32.0.0
- GEOS-11011 Upgrade postgresql from 42.4.3 to 42.6.0
- GEOS-11012 Upgrade commons-collections4 from 4.2 to 4.4
- GEOS-11018 Upgrade commons-lang3 from 3.8.1 to 3.12.0
- GEOS-11020 Add test scope to mockito-core dependency
- GEOS-11062 Upgrade httpclient from 4.5.13 to 4.5.14
- GEOS-11063 Upgrade httpcore from 4.4.10 to 4.4.16
- GEOS-11067 Upgrade wiremock to 2.35.0
For the complete list see 2.23.2 release notes.
About GeoServer 2.23 Series
Additional information on GeoServer 2.23 series:
GeoServer at FOSS4G 2023
The GeoServer team was pleased to attend FOSS4G 2023 last week (26 June - 2 July 2023) in Prizren, Kosovo!
FOSS4G 2023 was put on this year by the Open Source Geospatial Foundation (OSGeo) and the regional Free Libre Open Source Software Kosova (FLOSSK) organization. The local organizing committee worked very hard to make everyone feel welcome and well cared for. Thank you for hosting everyone, we had a great time.
GeoServer content:
- State of GeoServer 2.23
- GeoServer Feature Frenzy 2023
- GeoServer used in fun and interesting ways
- GeoServer Orientation
- Getting Started with GeoServer (Workshop)
GeoServer community content:
- FOSS4G 2023 (GeoCat Blog)
- GeoSolutions presence at FOSS4G 2023 in Prizren (Kosovo) (GeoSolutions Blog)
- Many additional presentations featured GeoServer and showcased its capabilities.
When videos are provided of the event we will update this post with links.

Prizren (Kosovo)
FOSS4G Code sprint
We also had our first scheduled codesprint on refactoring org.opengis package. The foss4g sprint was a fact-finding mission to establish the scope of work and confirm time frame and budget.
- The activity was successful in that we were able to change from org.opengis to org.geotools.api and write a script to update GeoWebCache and GeoServer projects.
- GeoServer has some difficulties as gs-printing and gs-geofence-server include the work of external projects which will require assistance.
The work is scheduled for the Bolsena Codesprint 2023 ahead of the GeoServer 2.24.0 release cycle.
For more information see OpenGIS Harmonization at OSGeo. If you are in a position to provide sponsorship, or in-kind participation, this activity could use your support.
GeoServer 2.22.4 Release
GeoServer 2.22.4 release is now available with downloads ( bin, war, windows) , along with docs and extensions.
This is a maintenance release of GeoServer providing existing installations with minor updates and bug fixes.
GeoServer 2.22.4 is made in conjunction with GeoTools 28.4.
Thanks to Peter Smythe (AfriGIS) and Jody Garnett (GeoCat) for making this release. This is Peter’s first time making a GeoServer release and we would like to thank him for volunteering.
Security Considerations
This release addresses security vulnerabilities and is considered an essential upgrade for production systems.
- CVE-2023-43795 WPS Server Side Request Forgery
- CVE-2023-41339 Unsecured WMS dynamic styling sld=url parameter affords blind unauthenticated SSRF
See project security policy for more information on how security vulnerabilities are managed.
Release notes
New Feature:
- GEOS-10949 Control remote resources accessed by GeoServer
Improvement:
- GEOS-10973 DWITHIN delegation to mongoDB
Bug:
- GEOS-8162 CSV Data store does not support relative store paths
- GEOS-10906 Authentication not sent if connection pooling activated
- GEOS-10936 YSLD and OGC API modules are incompatible
- GEOS-10969 Empty CQL_FILTER-parameter should be ignored
- GEOS-10975 JMS clustering reports error about ReferencedEnvelope type not being whitelisted in XStream
- GEOS-10980 CSS extension lacks ASM JARs as of 2.23.0, stops rendering layer when style references a file
- GEOS-10981 Slow CSW GetRecords requests with JDBC Configuration
- GEOS-10993 Disabled resources can cause incorrect CSW GetRecords response
- GEOS-10994 OOM due to too many dimensions when range requested
- GEOS-10998 LayerGroupContainmentCache is being rebuilt on each ApplicationEvent
- GEOS-11015 geopackage wfs output builds up tmp files over time
- GEOS-11024 metadata: add datetime field type to feature catalog
Task:
- GEOS-10987 Bump xalan:xalan and xalan:serializer from 2.7.2 to 2.7.3
- GEOS-11008) Update sqlite-jdbc from 3.34.0 to 3.41.2.2
- GEOS-11010 Upgrade guava from 30.1 to 32.0.0
- GEOS-11011 Upgrade postgresql from 42.4.3 to 42.6.0
- GEOS-11012 Upgrade commons-collections4 from 4.2 to 4.4
- GEOS-11018 Upgrade commons-lang3 from 3.8.1 to 3.12.0
- GEOS-11020 Add test scope to mockito-core dependency
Sub-task:
- GEOS-10989 Update spring.version from 5.2.23.RELEASE to 5.2.24.RELEASE
For the complete list see 2.22.4 release notes.
About GeoServer 2.22 Series
Additional information on GeoServer 2.22 series:
- GeoServer 2.22 User Manual
- Update Instructions
- Metadata extension
- CSW ISO Metadata extension
- State of GeoServer (FOSS4G Presentation)
- GeoServer Beginner Workshop (FOSS4G Workshop)
- Welcome page (User Guide)
Release notes: ( 2.22.4 | 2.22.3 | 2.22.2 | 2.22.1 | 2.22.0 | 2.22-RC | 2.22-M0 )
GeoServer 2.23.1 Release
GeoServer 2.23.1 release is now available with downloads (bin, war, windows), along with docs and extensions.
This is a stable release of GeoServer suitable for production systems, made in conjunction with GeoTools 29.1 and GeoWebCache 1.23.0.
We are grateful to Ian Turton (Astun Technology Ltd) for making this release.
Release notes
Improvement:
-
GEOS-10858 jdbc-config turns off isolated workspace support
-
GEOS-10898 Preserve key order in STAC responses coming from JSONB columns
-
GEOS-10923 Use default writing params on
GeoTIFFPPIO -
GEOS-10940 Update MapML viewer to release 0.11.0
Bug:
-
GEOS-8162 CSV Data store does not support relative store paths
-
GEOS-10837 geopackage output fails when
java.io.tmpdiron network share -
GEOS-10912 jms-cluster fails to clone grid coverage layer on other nodes
-
GEOS-10920 Excel output format packaging misses dependencies, cannot produce .xls
-
GEOS-10921 Double escaping of HTML with enabled features-templating
-
GEOS-10922 Features templating exception on text/plain format
-
GEOS-10932 csw-iso: should only add
'xsi:nil = false'attribute -
GEOS-10934 CSW does not show title/abstract on welcome page
-
GEOS-10946 WMS
GetLegendGraphicthrowsFootprintsTransformationcannot be cast toProcessFunctionException -
GEOS-10950 Performance regression in
DescribeFeatureTypeacross all feature types -
GEOS-10955 STAC templates are initialised in the wrong location
-
GEOS-10957 Support
ResourceAccessManagerimplementations returning custom subclasess ofAccessLimits -
GEOS-10969 Empty
CQL_FILTERparameter should be ignored -
GEOS-10975 JMS clustering reports error about
ReferencedEnvelopetype not being whitelisted in XStream -
GEOS-10985 B/R of GeoServer catalog is broken with GeoServer 2.23.0
Task:
- GEOS-10859 OGC API: swagger-api 4.15.5 upgrade
For the complete list see 2.23.1 release notes.
About GeoServer 2.23 Series
Additional information on GeoServer 2.23 series:
GeoServer 2.21.5 Release
GeoServer 2.21.5 release is now available with downloads (bin, war, windows), along with docs and extensions.
This is a maintenance release of the GeoServer 2.21.x series, made in conjunction with GeoTools 27.5 and GeoWebCache 1.21.5.
Thanks to Daniele Romagnoli (GeoSolutions) for making this release.
Security Considerations
2024-06-30 Update: The following mitigation has been provided:
-
CVE-2024-36401 Remote Code Execution (RCE) vulnerability in evaluating property name expressions (Critical)
geoserver-2.21.5-patches.zip (replacing
gt-app-schema,gt-complexandgt-xsd-corejars) has been provided by Andrea (GeoSolutions)
See project security policy for more information on how security vulnerabilities are managed.
Release notes
Bug
-
GEOS-3978 Layer configuration allows admin to enter a zero area bounding box
-
GEOS-6313 Lifecycle handlers not properly called during shutdown
-
GEOS-10006 Seeding GWC doesn’t work for layers with a dot in the name
-
GEOS-10500 WFS-T unable to delete more than 30 features in a single transaction when the data source is PostGIS
-
GEOS-10517 jms-cluster classes missing from XStream security configuration
-
GEOS-10593 Regression: Creating SQL View via REST API and explicit attribute list is no-longer possible
-
GEOS-10611 Uploading application/zip to styles endpoint does not clean up temporary files
-
GEOS-10828 OGC API - Features - Plugin breaks core `/rest` API with JSON payloads
-
GEOS-10837 geopackage output fails when java.io.tmpdir on network share
-
GEOS-10869 Jayway JSON Path libraries not included anymore on GeoServer packages
-
GEOS-10878 wps-multidimensional and wps-jdbc are not being deployed on maven repo
-
GEOS-10896 Missing NULL check in the template backwards mapping
-
GEOS-10899 Features template escapes twice HTML produced outputs
-
GEOS-10912 jms-cluster fails to clone grid coverage layer on other nodes
-
GEOS-10920 Excel output format packaging misses dependencies, cannot produce .xls
-
GEOS-10921 Double escaping of HTML with enabled features-templating
-
GEOS-10932 csw-iso: should only add ‘xsi:nil = false’ attribute
-
GEOS-10946 WMS GetLegendGraphic throws FootprintsTransformation cannot be cast to ProcessFunction Exception
-
GEOS-10950 Performance regression in DescribeFeatureType across all feature types
-
GEOS-10957 Support ResourceAccessManager implementations returning custom subclasess of AccessLimits
Improvement
-
GEOS-10870 Allow importer AttributesToPointGeometryTransform to preserve original geometries, and to configure the name of the target geometry
-
GEOS-10940 Update MapML viewer to release 0.11.0
Task
-
GEOS-10867 Bump commons-fileupload from 1.4 to 1.5
-
GEOS-10873 Upgrade XStream to 1.4.20
-
GEOS-10908 Update spring version from 5.2.22 to 5.2.23
-
GEOS-10863 Update Oracle JDBC driver to 19.18.0.0
-
GEOS-10904 Bump jettison from 1.5.3 to 1.5.4
For complete information see 2.22.5 release notes.
About GeoServer 2.21
Additional information on GeoServer 2.21 series:
Release notes: ( 2.21.5 | 2.21.4 | 2.21.3 | 2.21.2 | 2.21.1 | 2.21.0 | 2.21-RC )
Behind The Scenes
- GeoServer 3 First public release date
- GeoServer 3 Sprint Update
- GeoServer 2025 Q4 Developer Update
- GeoServer 3 Crowdfunding Goal Surpassed!
- GeoServer 2025 Q2 Developer Update
- GeoServer 3 Crowdfunding – Last Call!
- GeoServer 3 Crowdfunding Campaign Reaches Major Step: 80% Funding Completion
- GeoServer 2025 Roadmap
- GeoServer 2024 Q4 Developer Update
- GeoServer 3 Call for Crowdfunding